
Trashing and replacing hardware at the end of its life is important for your business’s day-to-day operation. Still, many may not realize it is also important for cyber security.
How are asset disposal and cyber security connected? In this article, we’ll discuss:
MSPs have to deal with disposing of hardware, but may not realize just how important the process of disposal really is.
At the same time, cybersecurity has become a priority for MSPs of all sizes. MSPs maintain backups, hardware, and client behaviors to make sure clients are safe.
So how are asset disposal and cybersecurity connected? IT Asset Disposal (ITAD). This is the erasure of data and disposing of hardware.
IT asset disposal goes beyond getting rid of hardware. It plays an important part in data security as well. Without a proper asset disposal strategy, data can easily be missed when assets at the end of their lifecycle are disposed of.
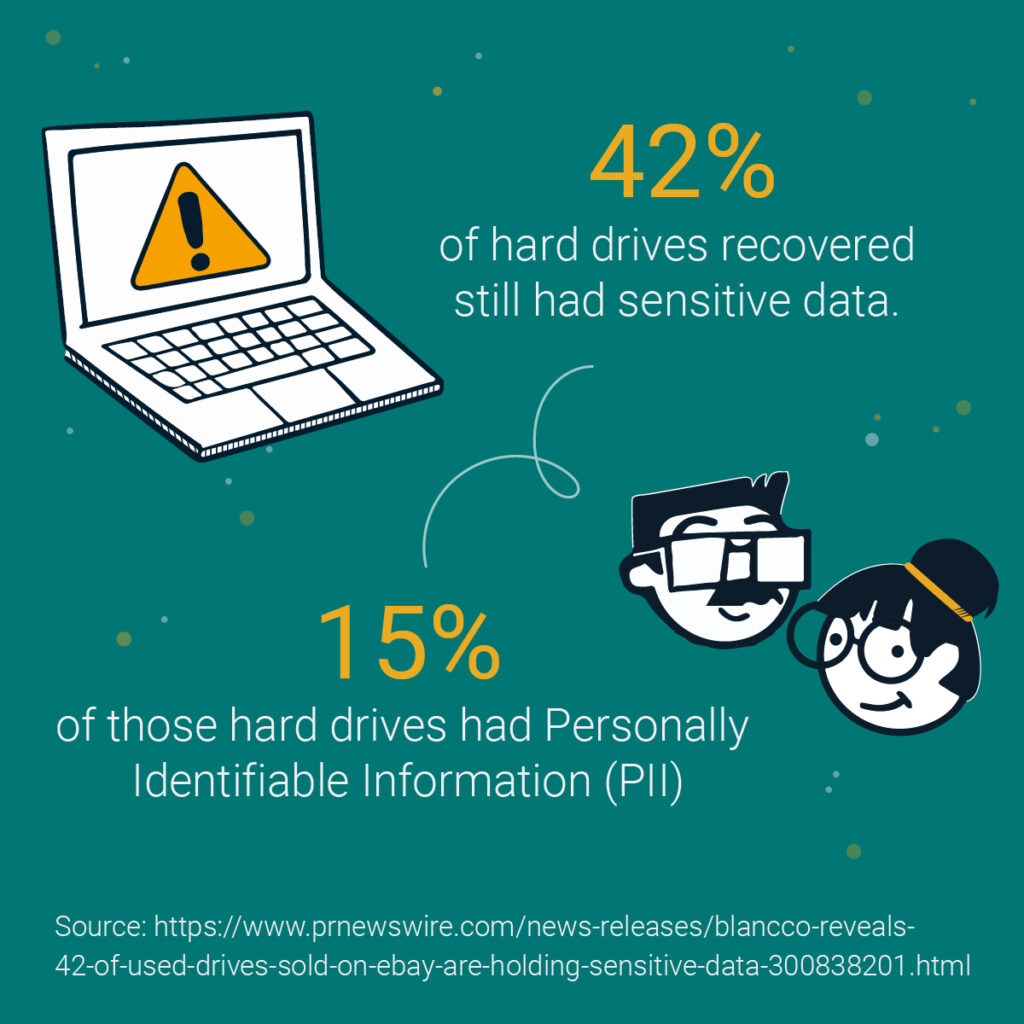
A 2019 study from data removal company Blannco showed that almost half of trashed hard drives had sensitive data that could be recovered.
Of the hard drives discovered in the study, one had sensitive data from a software developer. The developer had high level government security clearance.
The hard drive had scanned images of passports, birth certificates, and financial documents.
Other data included a freight company’s information and internal emails from a travel company.
Situations like these are why an IT asset disposal strategy is so important. A good strategy can let MSPs avoid these consequences and keep client data secure.
But what are the risks of not disposing of data properly? Your client could be damaged professionally and personally from data recovered from these assets. Your MSP will also suffer from potential legal action and a damaged reputation.
Mike Morrill, President of Total Solutions, makes disposing of clients assets a priority. Data breaches don’t just hurt clients, they hurt MSPs too.
“Once I take the asset, I have custody and control. They’ve trusted me and I’ve done whatever is appropriate. If I breach that, the minimum is my reputation takes a huge hit.”
A data breach could give a third party access to sensitive business information. That information could be used to damage a client or their business partners and customers.
Accessing Personally Identifiable Information (PII) can lead to financial fraud. A leaked social security number, bank account info, or phone number could result in large costs for the client.
Compromised data could also be used to maliciously attack your client or extort them.
MSPs and their clients may also be on the hook for violation of data protection laws and regulations.
Let’s take a look at how your MSP can avoid these risks and keep their clients safe.
A solid asset disposal policy won’t just keep clients safe, it’s a way for your MSP to deliver better service.
To provide better security, MSPs should look for methods that meet data disposal standards.
The National Institute of Standards and Technology (NIST) has a widely adopted standard for this reason. The NIST 800-88 guidelines are a standard that ensures proper erasure of data.
NIST 800-88 outlines the steps to protect against unauthorized data access. NIST outlines clearing and purging data, as well as destroying hardware.
Some clients work in industries that require compliance with government regulations, like Healthcare or Finance. Typically this means they must keep to strict data disposal requirements.
If they don’t dispose of data in a secure manner, they could be in breach of their compliance requirements and face fines.
Standards like NIST create an easy outline for MSPs to follow to make sure they meet their requirements.
MSPs should also make sure that IT asset disposal vendors provide certificates of destruction. Having confirmation documents will allow clients to trust their data was handled correctly.

It ensures they are keeping up with compliance requirements and will be a huge benefit in an audit. A destruction certificate can prove both MSP and client took steps to follow the regulations. This helps to protect them from compliance violations.
Whether it’s a malicious attack or human error, cyber liability insurance can protect your clients from costly damage. But qualifying for insurance can be tricky.
A survey done by BlackBerry and Corvus research showed that many businesses are underinsured. The 2022 survey included more than 400 IT and cybersecurity businesses.
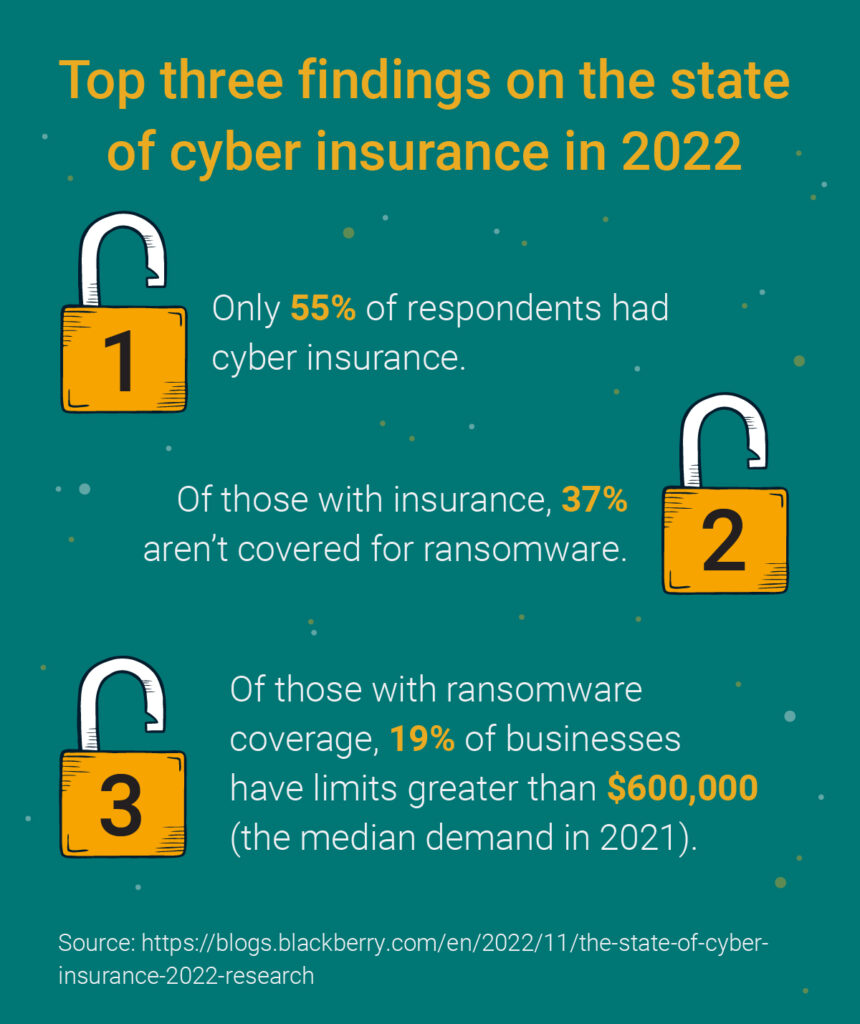
Businesses need more than just security measures in their daily operations. Disposing of assets is also a part of the security process.
Meeting compliance and getting a certificate of destruction can be the reason your client qualifies at all.
As President of Total Solutions, Morrill has seen the standards for businesses change. Insurance providers continue to increase the requirements to qualify for insurance, he said.
Businesses need to demonstrate that they follow the latest cybersecurity best practices.
That includes multi-factor authentication, endpoint threat detection, secure backups, and even asset disposal.
“Insurance providers are asking for more proof of validity. We’re starting to see the need to present logs for backups and logs on processes. They are going to make a compliance act for MSPs, that’s coming too,” he said.
“When you look at the grand picture, it impacts insurance premiums and ability to quality. I want to get rid of [these assets] in the fastest, most secure way I can.”
MSPs can prove their clients comply with industry regulations and follow a high standard of data security.
While insurance doesn’t stop the damage of improper data access, it can be a massive help to clients in recovery. It can save your clients finances in the event of a security breach and keep downtime to a minimum.
MSPs should always consider data security in all phases of the asset lifecycle.
While disposing of an asset seems like the end, that data can live on and cause problems later. Developing an asset disposal strategy to protect your clients shouldn’t be overlooked.
Approaching asset disposal with a strategic perspective is one way for MSPs to proactively mitigate security risks.
One simple way to ensure your disposal strategy is secure is with ScalePad IT Asset Disposal. Responsibly get rid of your assets all from within the Lifecycle Manager dashboard with our white glove service that takes care of packing and shipping for you.
With third party validation,data is erased to NIST 800-88 standards and you’ll receive a certificate of destruction upon completion. Record keeping in the app makes qualifying for cyber security insurance an easier process.
Put time into creating an asset disposal strategy now. This way you’ll have secure processes set in advance of your next hardware disposal project.
Streamline the asset disposal process with ScalePad’s IT asset disposal service in Lifecycle Manager.