Ignition 2026 was ScalePad’s future-focused virtual gathering built around this year’s theme: Success Unlocked and the idea that MSPs who stay ahead of changing compliance demands, rising customer expectations, and practical automation will be the ones that win in 2026 and beyond.
If you couldn’t join live (or want the highlights without rewatching every session), here are the key product announcements we shared.
Customer Success
See what was announced under our Customer Success portfolio, containing Lifecycle Manager and Quoter:
Deliverables that cut QBR prep time and boost client action
Launching today in Lifecycle Manager X, the updated Deliverables module gives you a consistent, client-ready presentation layer for QBRs, reports, and Customer Success conversations, so you spend less time assembling slides and more time driving outcomes.
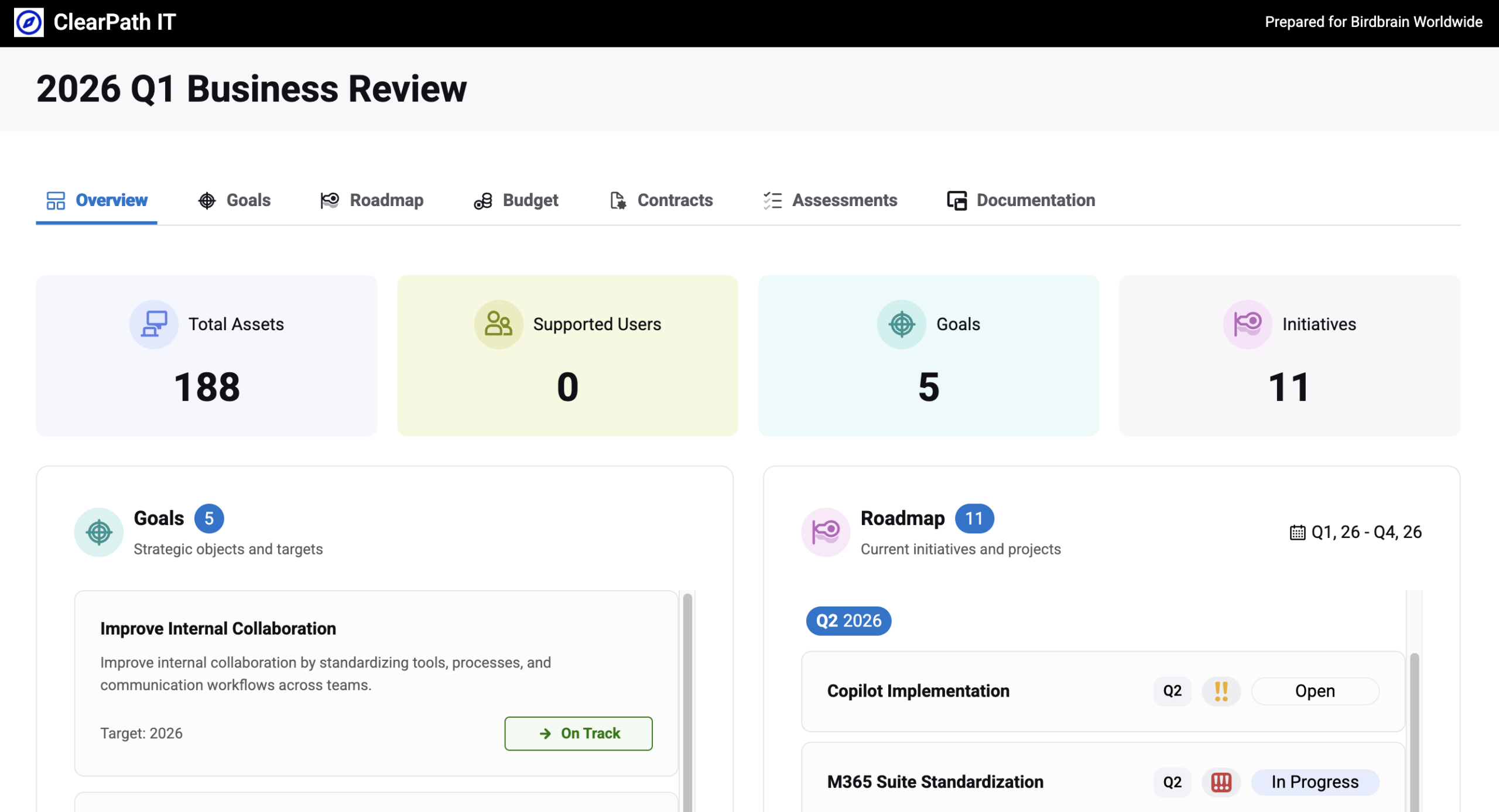
What’s new in Deliverables:
- Build richer QBRs with more report choices than ever before: You can now add more configurable sections from Lifecycle Manager. Drag in goals, budgets, assessments, and roadmaps; each section has controls like status, priority, and time range to tailor what appears.
- Give clients a modern, guided experience: Publish beautiful Deliverables that feel like a modern, easy-to-navigate web experience. Clear tabs across the top organize your story, with each tab highlighting key outcomes. This guides clients from where they are today to where they’re going together.
- Share and present in a few clicks: Send a password-protected link ahead of the meeting, present live in a white-labelled mode, or export to PDF for stakeholders who prefer attachments.
Deliverables integrations (launching now, expanding through 2026)
One of the biggest QBR pain points is vendor reporting, with every tool producing different formats, branding, and data that don’t connect cleanly to the story you’re trying to tell.
Deliverables integrations solve that by making vendor data plug-and-play inside your client narrative, launching with Cork, IT Glue, and Huntress, with broader vendor support rolling out throughout 2026. If you want a specific integration for your QBR reports, request it here.
All Client Analytics
You already have client-level visibility. But at Ignition, we announced All Client Analytics in Lifecycle Manager X. This global-view dashboard helps you understand what’s happening across your entire book of business.
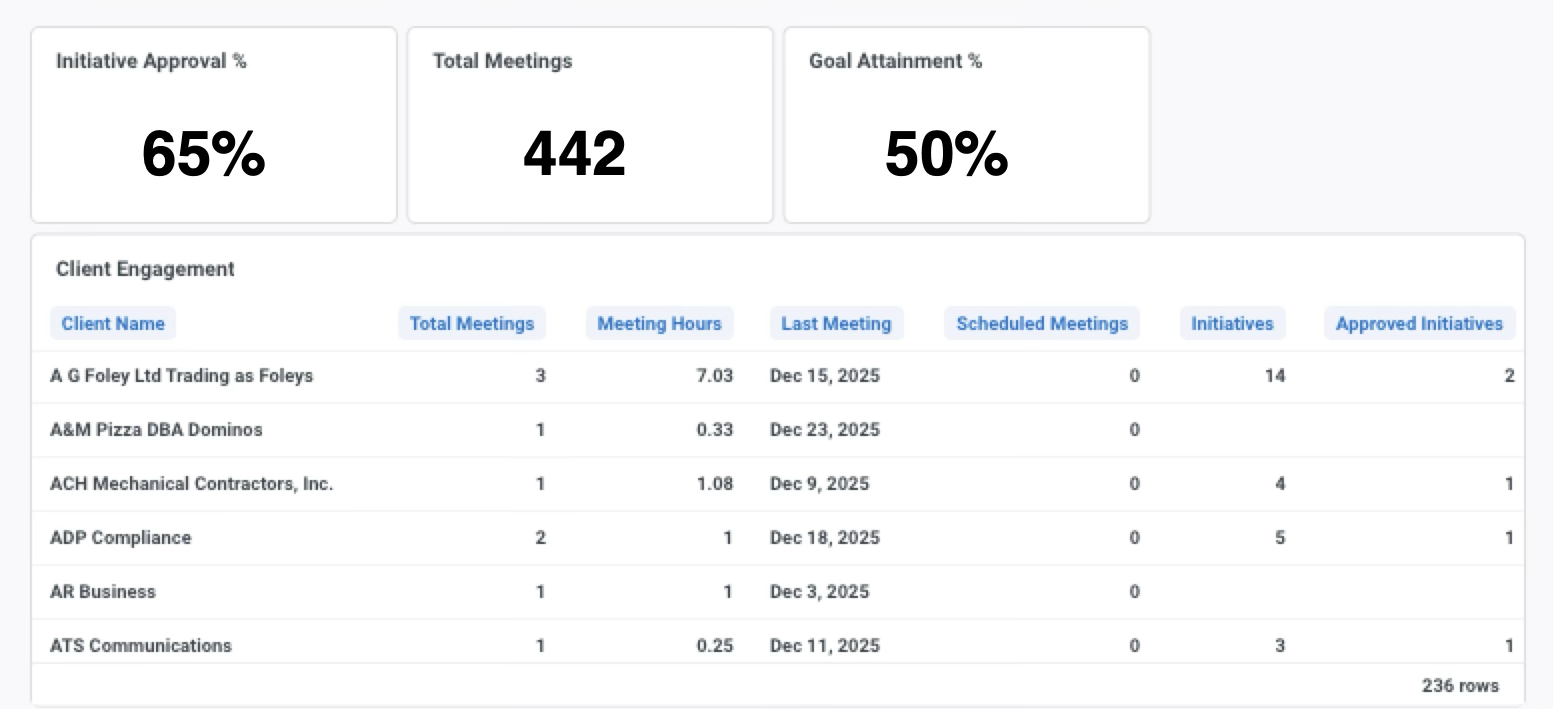
Global Analytics spans three areas:
- Service Quality: Analyze ticket trends to identify workload pressure, under-servicing risk, and areas with the greatest delivery strain.
- Client Experience: Spot experience outliers, understand customer satisfaction trends, and prioritize where attention is needed.
- Client Engagement: See engagement activity across clients to identify signals such as meeting frequency, time spent, and whether recommendations are being approved.
And it’s all building toward what’s coming later in 2026: a true Client Health Index, where Service Quality, Engagement and Experience become clear pillars that show which clients are healthy, which aren’t, and why.
Quote Linking in LM
Platform unification is a major theme for 2026, and we announced a big step forward with the new workflow between Quoter and Lifecycle Manager.
With quote linking available today, you can connect a quote in Quoter to the specific Initiative it supports in Lifecycle Manager. This creates a more consistent workflow for teams that want planning, proposals, and outcomes to stay aligned.
- You can select the correct Initiative when preparing a quote in Quoter.
- You can open the related Initiative in Lifecycle Manager directly from Quoter.
- You can view whether a quote exists for an Initiative and its status from within Lifecycle Manager.
This launch is also an early example of the platform direction we shared for 2026, where cross-product workflows become more connected, and data entry happens once. Quote linking reduces copy-and-paste work and helps account teams stay coordinated from planning through execution.
Next, we are working toward the ability to create and link quotes directly from Lifecycle Manager Initiatives, so the workflow becomes even more seamless for account teams and vCIOs.
Risk
ControlMap AI

Compliance requirements are accelerating globally, and what used to apply only to the enterprise is now landing squarely in the mid-market. MSPs are at the center of that shift, and ControlMap is doubling down on automating, contextualizing, and scaling compliance as you help more of your clients get certified.
At Ignition, we highlighted the next leap: ControlMap AI. It’s our roadmap toward agentic compliance.
Coming this quarter, you’ll get access to a Security Questionnaire Agent that helps draft and refine responses to security questionnaires.
AI is only as good as the data behind it, and ControlMap already contains the structured context that makes AI useful: frameworks, assessments, risks, policies, assets, vendors, evidence, and how they connect.
Backup Plans
Backups are the lifeline; missing one is not an option. But MSPs manage hundreds (or thousands) of backup jobs across multiple tools. Historically, this means spreadsheets, noisy email alerts, and too much time spent validating what worked.
That’s why we announced Backup Plans in Backup Radar.
Backup Plans is a significant enhancement designed to help MSPs define “success” for each client —and prove it.
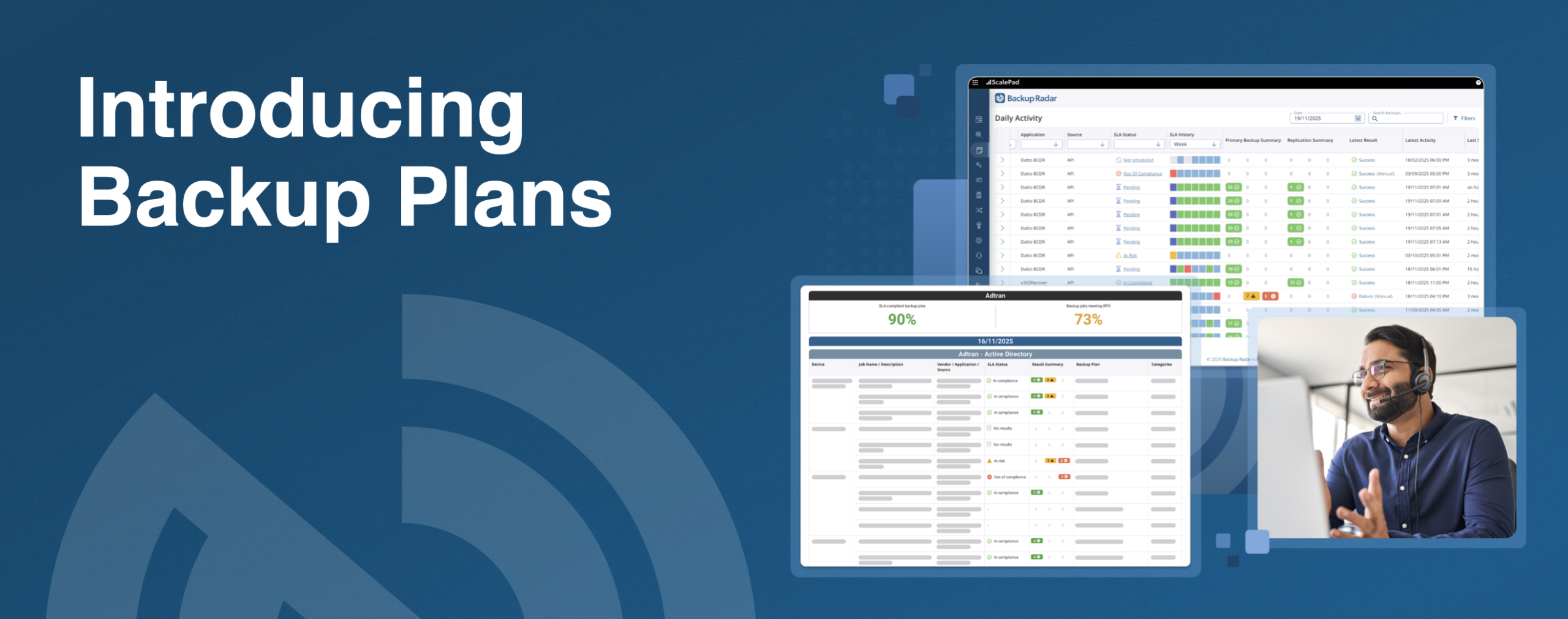
With Backup Plans, you can:
- Set SLAs per backup: Define what “successful” actually means for that client/workload.
- Set RPOs for backups: Align with risk tolerance and business impact.
- Produce stronger, compliance-ready reporting that clearly communicates risk and readiness.
- Monitor in real time without drowning in noise or false positives.
We also gave a sneak peek at what’s ahead: tighter alignment between backup performance and compliance outcomes — so SLA/RPO performance can map cleanly into reporting and readiness conversations.
We’re continuing a phased rollout of Backup Plans for all Backup Radar users. If you’d like access sooner, please contact your ScalePad account manager.
ScalePad API
At Ignition, we introduced the ScalePad API as the foundation for a more open, automation-ready platform, built on the same normalized and enriched client data that powers ScalePad products.
Instead of forcing you to stitch together dozens of vendor APIs and reconcile mismatched data models, the ScalePad API gives you a single, consistent way to work with client information and then take action across products.
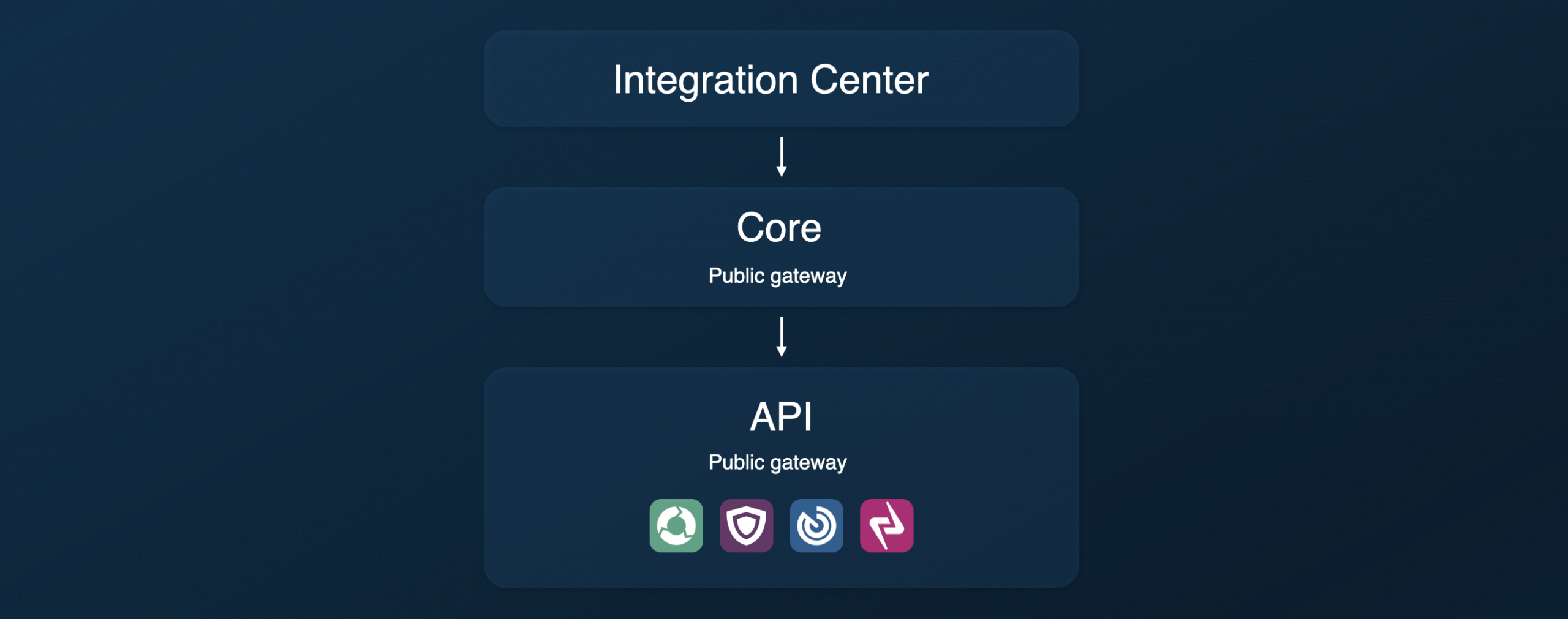
The API is purposely split into two layers:
- The Core ScalePad API is your gateway into the shared ScalePad “system of record” for client data. It exposes common objects like clients and contracts in a consistent model that stays the same no matter which upstream tools you connect. This is the API you use when you want reliable client context that can power cross-product workflows and external systems without re-mapping everything for each tool.
- Product-specific APIs go deeper into what each product can do. These APIs are where you access specialized actions and objects that only exist inside a given product, such as Lifecycle Manager X, ControlMap, or Quoter. Product APIs are designed to mirror real workflows you would normally perform in the UI, so you can automate the same operations programmatically while still benefiting from the shared client model underneath.
In practice, the split looks like this. You use the Core API to identify the right client and retrieve clean, standardized client context. Then, use a product API to execute a product-specific workflow for that client.
Want the full walkthrough?
If you want to see any of these features in action, catch the on-demand sessions or book time with the team.
And if you have a feature request, please submit a product idea in our community. Partner feedback continues to shape what we build next.
We’ve released a set of highly requested improvements to the Audit module designed to make audit preparation faster, clearer, and easier for MSPs managing client compliance. These updates help you cut manual work, reduce audit back-and-forth, and provide auditors exactly what they need in a format they understand. Here’s what’s new:
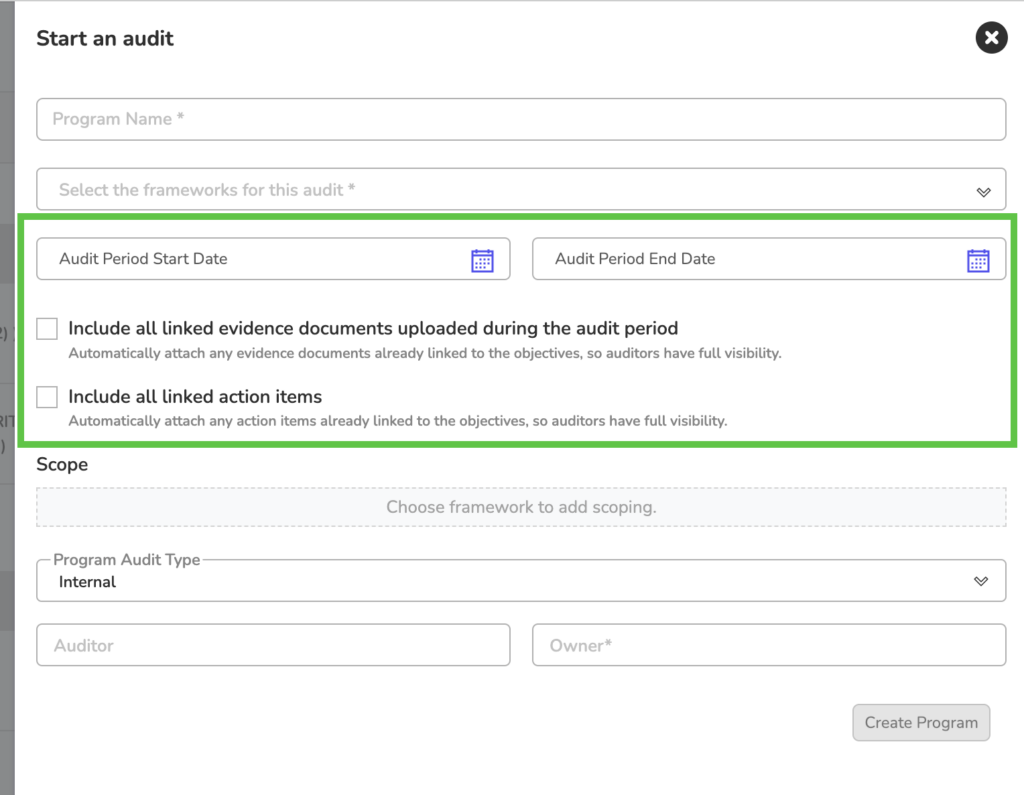
Import Evidence Automatically When You Start an Audit
You can now choose a start date when creating an audit and automatically import all relevant evidence from that period. You decide what to include:
• Evidence documents already linked to framework objectives
• Linked action items from the same date range
This helps improve the workflow, saving manual work and ensuring everything is neatly pulled in at the beginning of the audit.
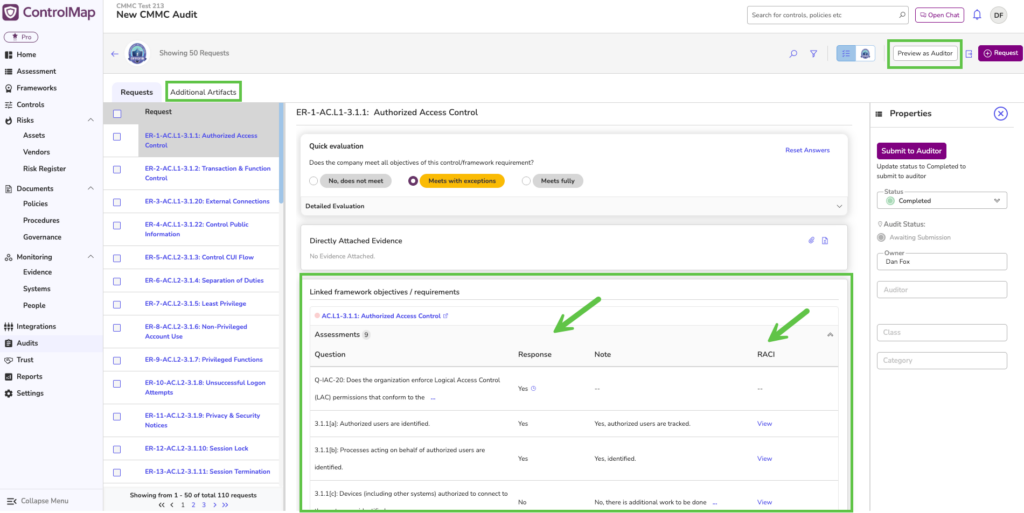
CMMC-Specific Improvements: Sub-Objectives in Audit
CMMC assessors don’t score the top-level objectives. They score the sub-objectives. ControlMap has supported this workflow for years, making it a popular choice in the CMMC community. That unique sub-objective workflow has been added to the audit feature set.
You’ll now see linked sub-objectives directly within the audit, making it easier to prepare clients for how assessors actually evaluate their environment. Nothing gets lost at the high level, and you always know exactly what mapping reviewers will look at.
Some additional CMMC enhancements include CUI mapping within the Assets tab, the Additional Artifacts feature within audit and look for updates to CMMC 2.0 to include new content from the CMMC 2.13 assessment guide for Level 1 and Level 2.
Preview as Auditor
This was one of the most requested audit features within the community. You can now preview the audit exactly as your auditor will see it.
This helps you catch gaps early, verify your evidence layout, and walk into the assessment confident that everything is clear and easy to review.
Better Control of Scope
Two improvements make defining and adjusting scope far more flexible:
• Scoped Requirements: Choose whether to include all in-scope requirements or select specific ones when creating an audit program.
• Update Scope: Update the scope for one or multiple audit programs at any time without recreating anything from scratch.
Manage Artifacts at the Program Level
You can now map and un-map artifacts such as documents and reports directly at the program level. This makes it simpler to standardize your audit packages across clients and frameworks, and is particularly useful for CMMC, where large reports such as the SSP or SPRS score, may need to be included at the framework or top level.
Directly Attach Evidence to Requests
A new option lets you upload evidence files directly within an audit request. No more jumping between sections to attach supporting documents.
Evidence Document Enhancements
Evidence documents can now be attached directly to requirements from within the audit. This provides you a streamlined workflow when preparing for internal or third-party reviews.
Additional Improvements
• Question History: Review the full history of assessment questions for better audit traceability.
• User Limit Increase for Free Plan: Free accounts now support up to 2 admin users.
• Collapsible Menu: Previously available only on Pro, now available for Free and Essentials plans for easier navigation.
What This Means for MSPs
These enhancements make it easier to:
• Prep clients for audits with less manual effort
• Align more accurately with CMMC assessor expectations
• Standardize audit workflows across frameworks and clients
• Give auditors a clean, professional review experience
• Reduce the time from audit kickoff to completion
If you’re already using the Audit module, these updates are live in your account. If you’re considering offering audit support as part of your compliance services, this release gives you a stronger, more efficient foundation to build upon.
See it in action: Log in to ControlMap or book a demo.
For more details on updates made in ControlMap, view the full release notes.
Managing compliance year after year just got easier. ControlMap’s new Assessment Snapshots feature lets you refresh, compare, and update client assessments without starting from scratch.
MSPs told us that refreshing assessments each year was repetitive and time-consuming. With Assessment Snapshots, you can now:
- Take a Snapshot to preserve a point-in-time record

- Refresh Answers and keep, clear, or update them as needed
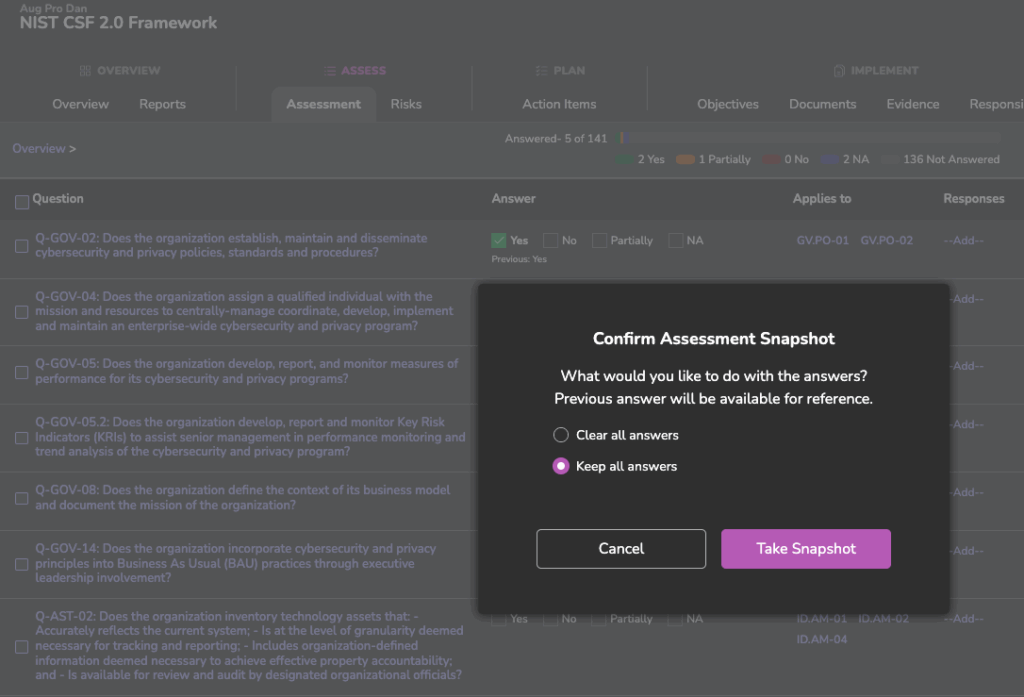
- Update Scores & Reports instantly
- View & Restore Snapshots for historical comparison
- Leverage Notes & Answer History to capture context over time
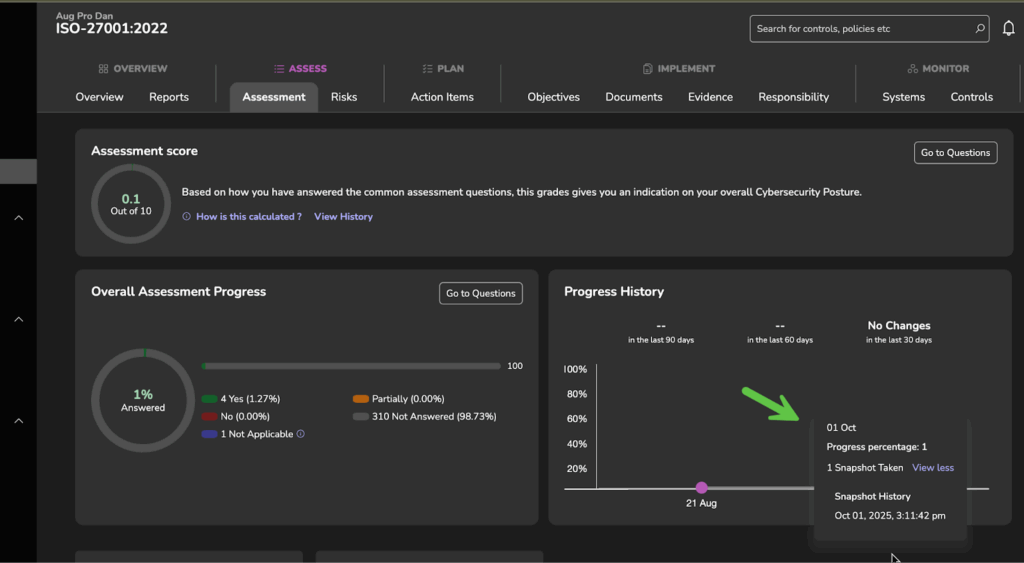
The result
Save hours of manual re-entry while keeping a full audit trail. Snapshots make annual reassessments faster, more accurate, and easier to explain to clients and auditors.
Available now
You’ll find the new Refresh button on the Assessment page by framework. Available for Essentials and Pro tiers (not available in Free).
See it in action: Log in to ControlMap or book a demo.
For more details on updates made in ControlMap, view the full release notes.
For MSPs, the fastest way to prove compliance value is to show it. With ControlMap Free, you can assess a client against a framework and share a report all without a cost or contract.
When you’re ready to deliver ongoing vCISO services for a client, ControlMap Essentials gives you the next step without jumping straight to multi-framework, audit-ready ControlMap Pro.
ControlMap Free
ControlMap Free lets you start delivering compliance services without a financial commitment. You can run an assessment, track key items like policies, risks, and evidence in one place. It’s a practical way to prove value to a client before deciding to expand compliance services.
Frameworks
Choose one from these 10 open frameworks:
- NIST Cybersecurity Framework (CSF)
- HIPAA Security
- CIS Critical Security Controls
- GTIA Cybersecurity Trustmark
- Cyber Essentials UK
- Australia’s Essential 8
- CyberSecure Canada
- FINRA Cybersecurity
- NIST AI
- NIST Privacy
Key capabilities
- Run assessments
- 10 policies with built-in templates
- 10 risks from a preloaded risk set
- 10 evidence items
- One report
- One ScalePad integration
- Single admin user
Best for:
- Offering compliance assessments as a lead-in to vCISO services
- Building credibility with prospects before they buy
- Showing structured, professional reports from day one
ControlMap Essentials
ControlMap Essentials gives MSPs everything needed to deliver full compliance assessments for one framework, with unlimited policies, risks, and controls. It’s designed for those ready to move past the basics but not yet in need of full Pro capabilities.
Frameworks
One framework from the full library of 60+ (excluding frameworks with controls)
Key capabilities
- Unlimited policies, risks, and evidence
- Full reporting
- Unlimited admin users
- Full Compliance Dashboard
- Audit Templates & Audit Readiness
Best for:
- Standardizing compliance services for a single framework
- Offering more than assessments, with full documentation and governance
- Building recurring compliance revenue before scaling to Pro
Compare the tiers
To see a full features comparison table, check out our pricing page.
Start Your First Client Assessment
Set up your first client in and run an assessment without touching a spreadsheet. With Free, you’ll use one of the 10 most common frameworks to show value fast. When you’re ready for unlimited policies, risks, and evidence and need a wider range of frameworks to choose from, Essentials is the next step.
Try ControlMap Free or Essentials or See the new tiers on our pricing page.
We’re celebrating Canada Day with two product updates to ControlMap 🇨🇦
- A new Canada Region option when setting up client tenants
- An updated version of the CyberSecure Canada framework
These updates help meet local data residency expectations and stay aligned with evolving national certification standards.
Host Client Data in the Canada Region With ControlMap
You can now select Canada as a hosting region when creating or editing client tenants inside ControlMap. This expands our global region support to:
- United States (Default)
- United States – GovCloud
- Europe (EU)
- Australia (AU)
- Canada (CA) 🇨🇦
This addition supports MSPs working with clients that have strict data residency requirements, common in sectors like finance, healthcare, and government. ControlMap is hosted on AWS infrastructure, and the new Canadian region ensures data remains within national borders.
CyberSecure Canada Framework Updated to Latest Version
The CyberSecure Canada framework in ControlMap has been updated to reflect the latest release from the Canadian government. This update includes refinements to control language, framework structure, and implementation guidance.
CyberSecure Canada is a nationally recognized cybersecurity certification program designed to help small and medium-sized businesses (SMBs) adopt baseline cybersecurity practices. It draws from globally accepted standards like ISO 27001 and NIST.
With ControlMap, MSPs can operationalize the framework efficiently through:
- Updated and pre-mapped controls
- Built-in policy templates and audit-ready documentation
- Automated evidence tracking and reporting
Whether your clients are pursuing CyberSecure Canada certification or simply aligning to its principles, this update ensures your services are built on the most accurate and current version of the framework.
Both Updates Available Now in ControlMap
These enhancements are now live and available in ControlMap. For guidance on how to select the Canada Region or navigate the updated CyberSecure Canada framework, visit our Help Center.
Ready to support Canadian clients with local hosting and updated controls? Book a demo to see how ControlMap can help.
For more details on updates made in ControlMap, view the full release notes.
ControlMap has just rolled out support for the latest version of the Secure Controls Framework: SCF 2025.1.1. This framework helps you manage and align your clients with multiple regulatory requirements simultaneously, from ISO 27001 and SOC 2 to NIST and CMMC.
If your clients operate in regulated industries like healthcare, finance, education, or government, the SCF is one of the most efficient ways to unify overlapping requirements under a single, streamlined control set.

What’s New in SCF 2025.1.1?
1. Control Enhancements Across 33 Domains
The SCF 2025.1.1 release includes 1,076 detailed controls, offering clearer, more actionable guidance across critical areas like:
- AI risk and governance
- Supply chain and vendor management
- Data privacy and classification
- Security program governance
2. Refreshed Framework Mappings
This release includes updated crosswalks to industry standards and regulations, like:
- ISO/IEC 27001:2022
- NIST Cybersecurity Framework (CSF) 2.0
- CMMC 2.0
- SOC 2, PCI DSS, HIPAA, and more
ControlMap automatically cross-maps controls across frameworks, so you can reuse evidence, reduce redundant tasks, and streamline audits across your entire client base.
3. Updated Domain Definitions & Structure
Several domains, including Governance, Risk, Privacy, and Vendor Management, have been refined for clarity and consistency. These structural updates make it easier to understand what’s required, how to implement controls, and how to communicate progress to your clients.
4. Improved Implementation Guidance
The updated SCF includes expanded guidance on interpreting and applying controls in real-world client environments. Combined with ControlMap’s built-in:
- Policy templates
- Evidence collection automations
- Audit-ready reporting
...you’ll spend less time translating compliance frameworks and more time delivering results your clients can see.
Explore the SCF 2025.1.1 in ControlMap
ControlMap automates the heavy lifting of framework updates, so you can focus on scaling your services, not managing spreadsheets. Book a demo to explore how SCF 2025.1.1 works inside ControlMap.
For more details on updates made in ControlMap, view the full release notes.
The NIS2 Directive is a major legislative update passed by the European Union to strengthen cybersecurity across critical and digital infrastructure. Now available in ControlMap, this framework helps MSPs guide their clients through NIS2 compliance using pre-built content, automated workflows, and audit-ready reporting.
What is the NIS2 Directive?
NIS2 (Directive (EU) 2022/2555) establishes baseline cybersecurity and incident reporting obligations for a wide range of essential and important entities across the EU. This includes sectors such as energy, healthcare, finance, digital infrastructure, public administration, and more.
The Directive introduces stricter governance rules, such as board-level accountability, supply chain risk management, mandatory breach reporting within 24 hours, and oversight by national supervisory authorities. It applies to both EU-based companies and those outside the EU that provide services in the EU.
Organizations that fail to comply face penalties, including fines and reputational damage, making proactive compliance support from MSPs more critical than ever.
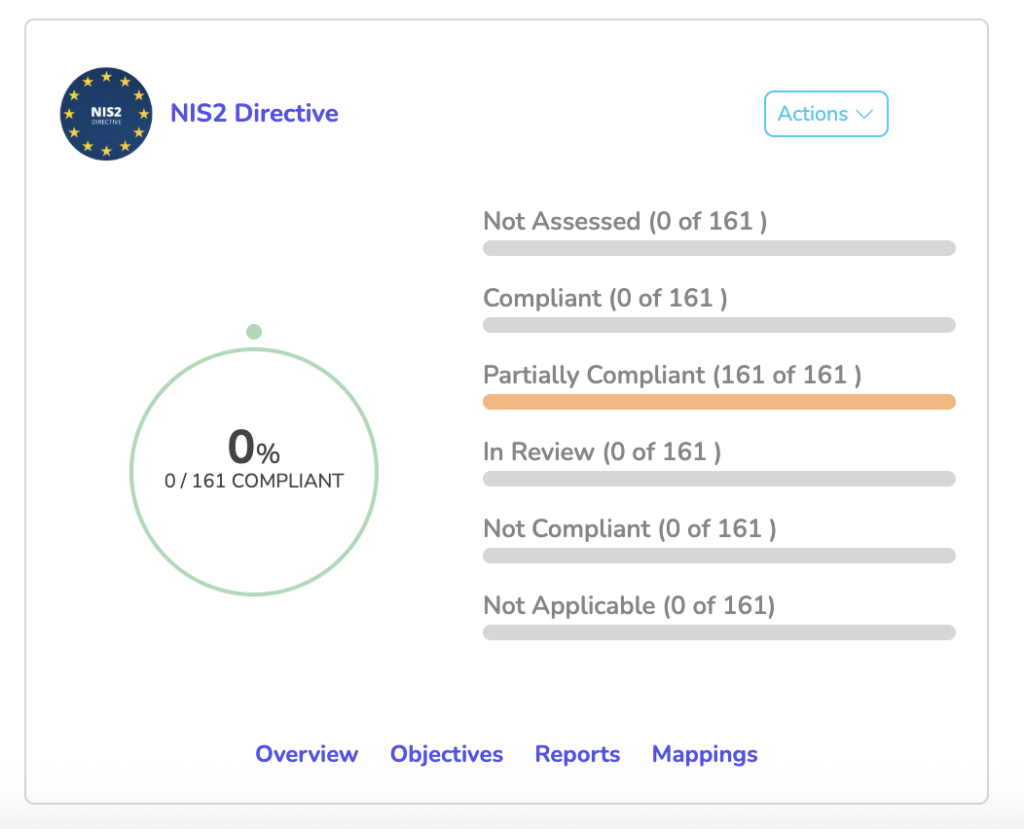
Key Benefits of NIS2 in ControlMap
Launch NIS2 compliance programs faster. Use a structured, ready-to-deploy framework to get clients onboarded without starting from scratch.
Save time with pre-mapped policies and controls. Access NIS2-aligned templates for policies, risks, and controls to eliminate setup delays.
Reduce effort with cross-framework mapping. Leverage built-in mappings to ISO, NIST, and more so your work scales across clients and industries.
Stay audit-ready with real-time visibility. Monitor compliance status, close gaps quickly, and generate regulator-ready reports on demand.
Grow in high-demand verticals. Support clients in sectors like healthcare, finance, and digital infrastructure where NIS2 is now required.
NIS2 Directive is for MSPs Who:
- Support clients based in or serving the EU
- Have clients in regulated sectors: energy, water, transport, finance, healthcare, digital infrastructure, public administration, space, and more
- Are looking to grow vCISO or compliance-as-a-service offerings tied to current legislation
Start helping clients meet NIS2 requirements
You can now import the full NIS2 Directive into your clients’ tenants, map it to existing frameworks, and deliver a fully audit-ready compliance program. Log in to ControlMap to get started.
Request a demo to see how NIS2 fits into your CaaS or vCISO services if you want help integrating NIS2 into your CaaS or vCISO offering.
For more details on updates made in ControlMap, view the full release notes.
You can now generate polished, client-facing reports directly from the Executive Dashboard in ControlMap. These Compliance Health Reports are purpose-built for QBRs (quarterly business reviews) and status updates, helping you clearly communicate completed work, current status, and areas that need attention.
Each report combines assessment progress, framework completion, documentation, risk posture, and upcoming tasks, giving your clients a comprehensive view of their compliance journey without manual tracking or formatting. Reports can be customized and automated to save you time and help improve your engagement with your client. Just customize your content how you like, set a schedule (weekly/monthly, etc.), save, and go!
What’s Inside
📊 Compliance Health Score
The report opens with a single score out of 100, summarizing overall compliance posture. This number reflects a combination of assessment results, documentation status, and evidence completeness, providing an instant snapshot of performance over time.
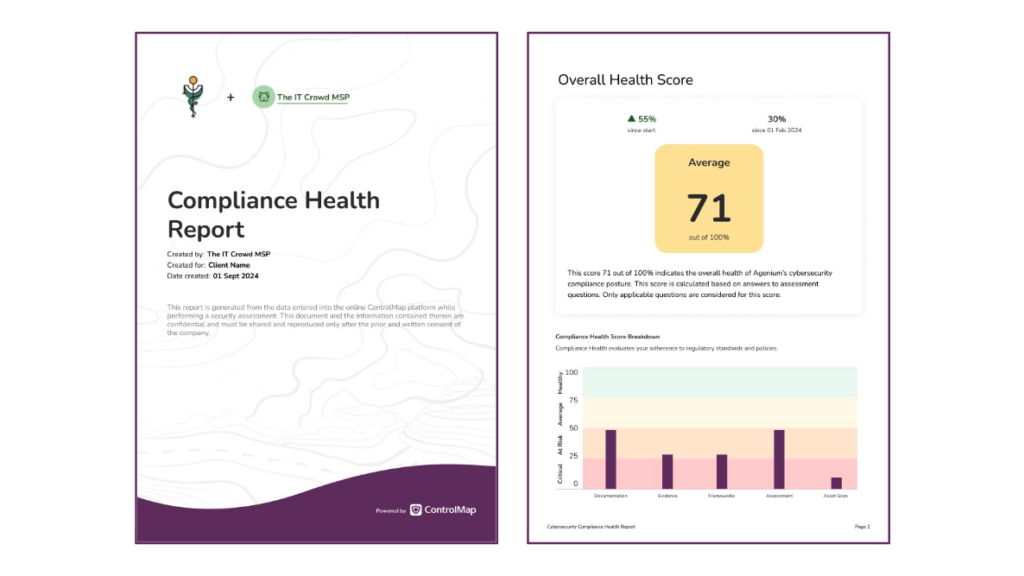
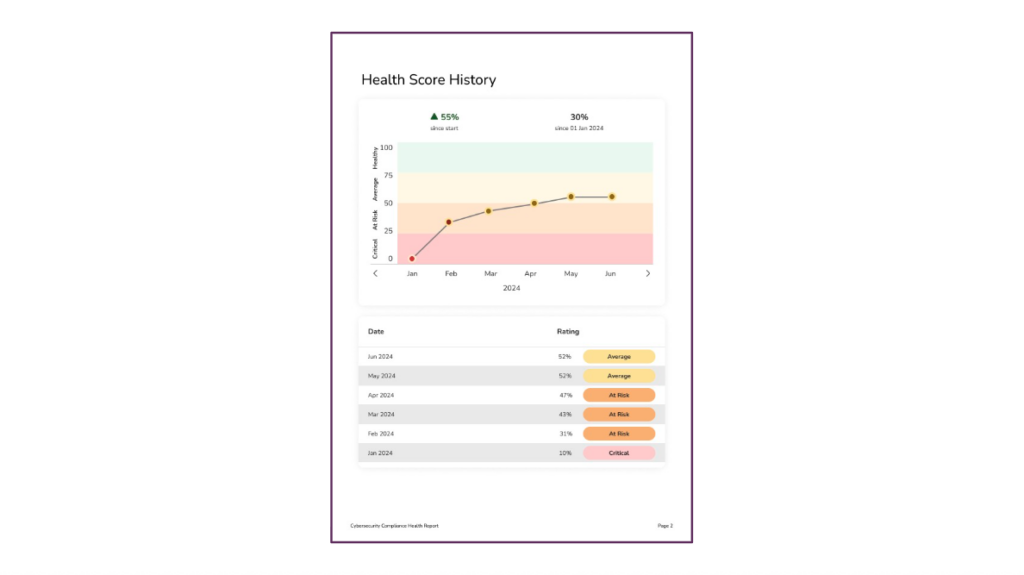
📉 Health Score History
A timeline view shows changes in the compliance score across the past several months. These trendlines make it easy to highlight progress or identify periods where efforts may have stalled.
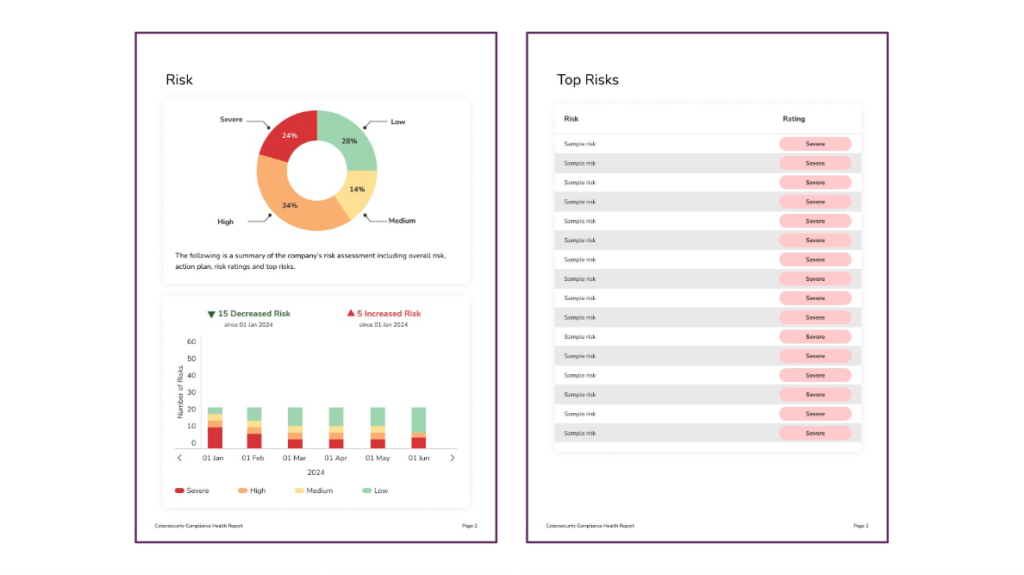
🚨 Top Risks and Risk Distribution
The report summarizes the most critical risks by severity and visualizes how risk exposure has shifted over time. This section also includes counts of increased or decreased risks, giving you a way to frame both wins and areas of focus for the next period.
📚 Framework Progress Tracking
Progress toward each active framework, like NIST 800-171, ISO 27001, or HIPAA, is broken down by percentage and tracked over time. This helps reinforce the specific frameworks each client is working toward and how close they are to completion.
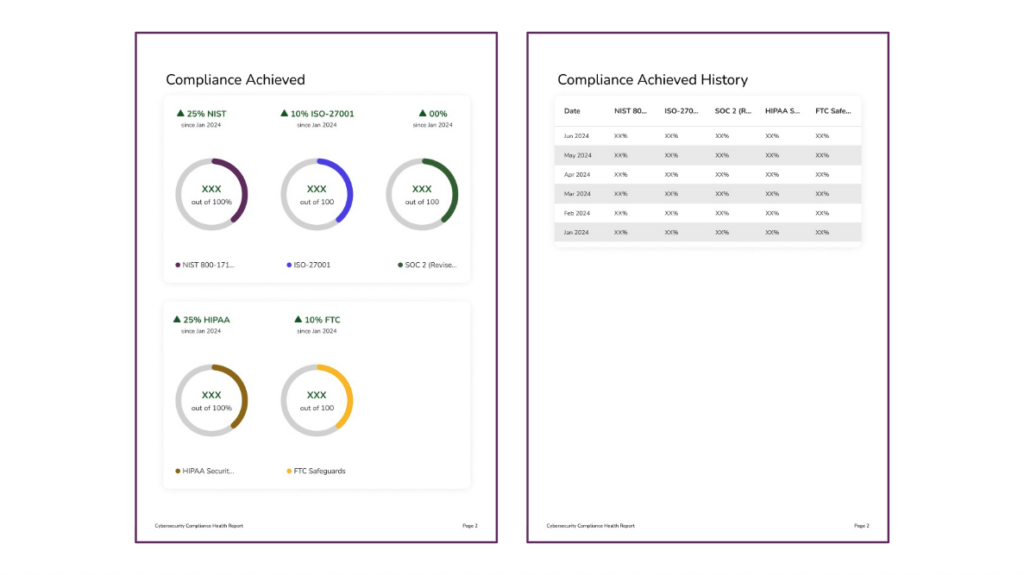
✅ Assessment Completion
This section shows the number of assessment items marked as Yes, Partially, No, or Not Applicable, paired with historical trends and a list of recent changes.
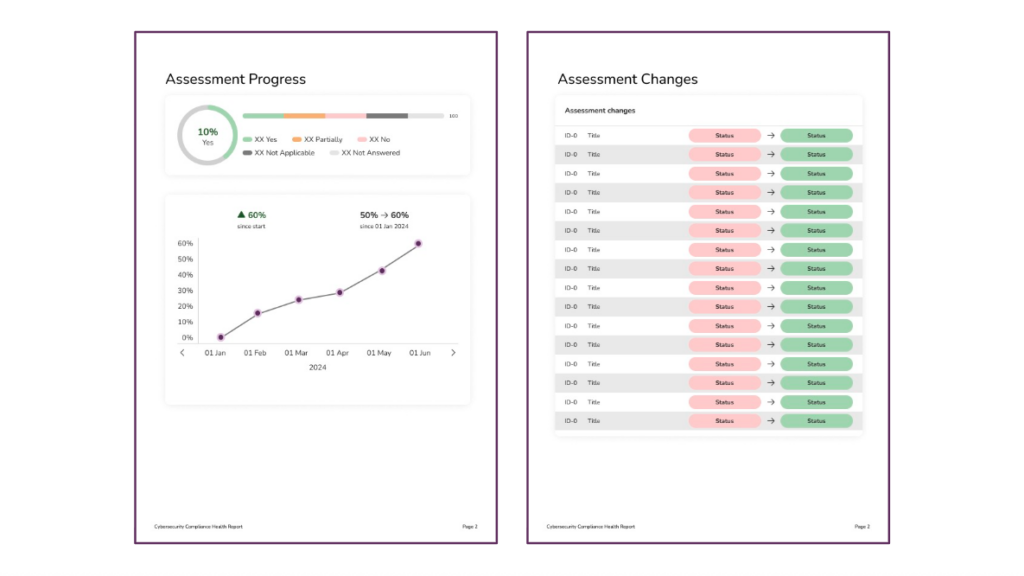
🎯 Objectives Progress
Displays the current status of objectives across Compliant, Partially Compliant, Not Compliant, and other states. Progress is graphed over time, helping visualize how maturity is evolving.
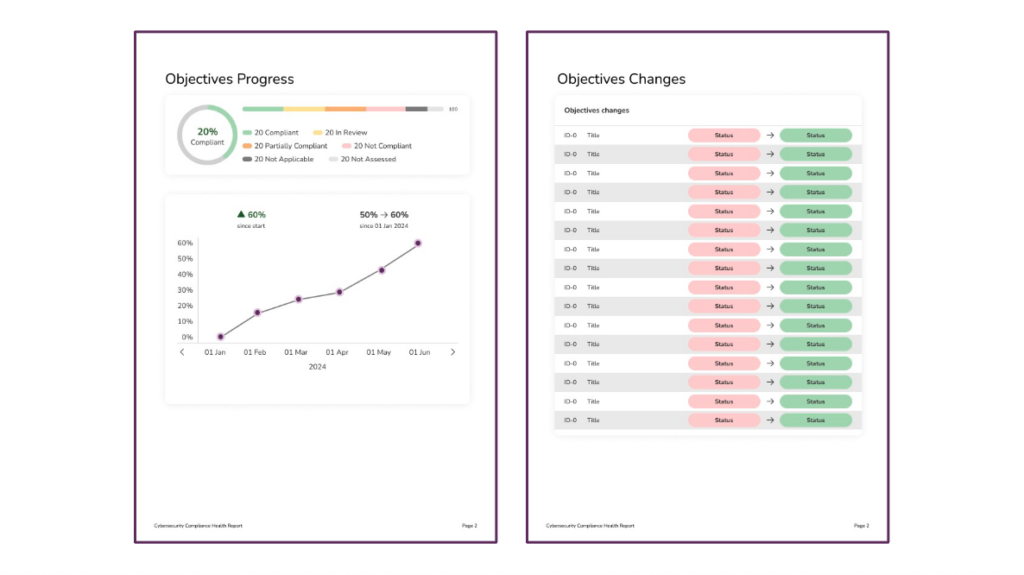
🛠️ Action Items Progress
This section tracks the status of all action items across the organization, highlighting how many are completed, in progress, in review, or not yet started. Showing trends over time helps teams stay accountable and aligned on what’s been done—and what still needs attention.
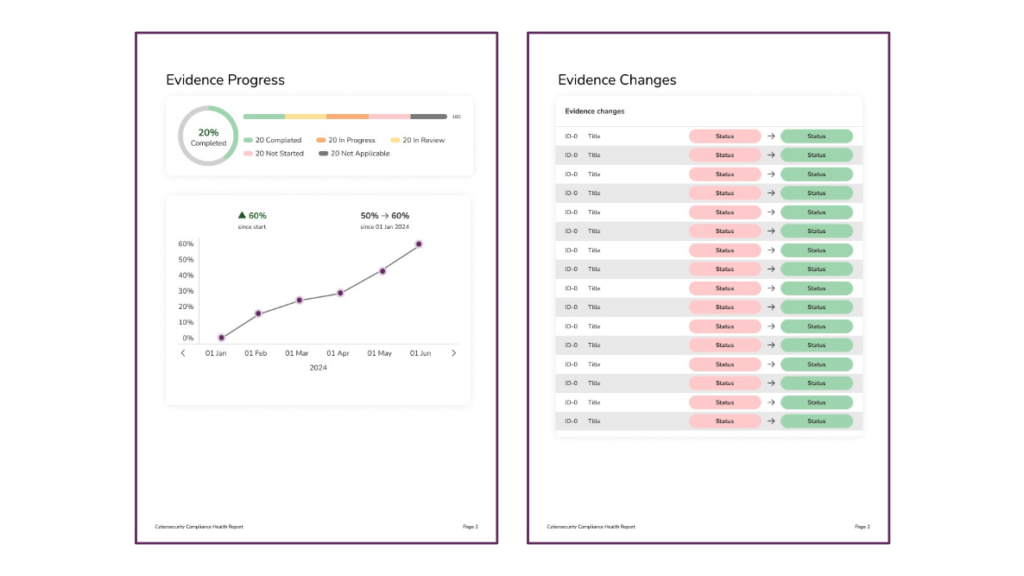
📂 Evidence Collection
This section shows how many pieces of evidence have been collected, are in progress, or remain incomplete. Since documentation is a critical component for audit readiness, this section helps identify where gaps still exist.
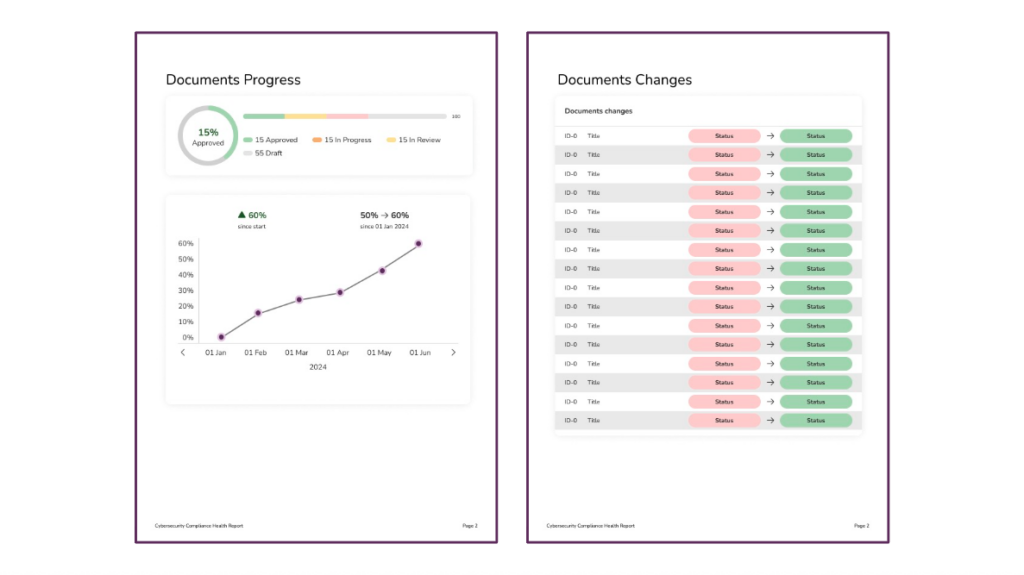
📁 Policy & Document Status
Tracks how many documents are in draft, under review, in progress, or fully approved. A separate table outlines recent updates to help teams track change activity.
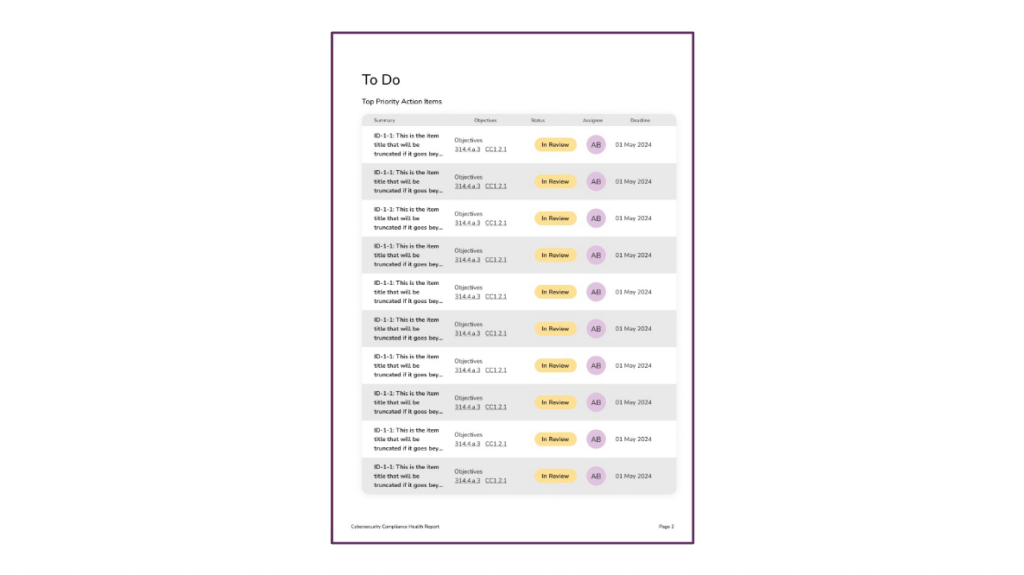
📅 To Do: Top Priority Action Items
The report closes with a summary of high-priority action items, including objective references, current status, assignees, and deadlines.
How to Use It
- Export reports as Word DOC or PDFs from the Executive Dashboard to share during client meetings or reviews.
- Use month-over-month trend visuals to show progress and highlight upcoming needs.
- Share framework-specific insights to support strategic compliance planning.
- Reference open risks and outstanding tasks to guide next steps and follow-ups.
- Customize your content with a built-in editor and customization options.
- Schedule for recurring automatically to self or client as desired
Available Now
Compliance Health Reports are now live within Reports and the Executive Dashboard in ControlMap. Log in now to try it out—or book a demo to see how it works.
Coming Soon
With the new reporting design and technology introduced with the Compliance Health Report, the existing Assessment Report in ControlMap is also getting a visual refresh to match the new, polished look. While the content and structure will remain familiar, the updated design brings visual consistency across reports, making everything look sharper for client-facing use.
For more details on updates made in ControlMap, view the full release notes.
ScalePad is proud to announce SOC 2 Type II and ISO 27001 compliance certifications for its products Lifecycle Manager, Lifecycle Insights, Backup Radar, ControlMap, and newly certified for 2025, Quoter. This milestone reinforces ScalePad's unwavering dedication to upholding the highest data security, privacy, and integrity standards for its global customer base.
New for 2025: Quoter
SOC 2 Type II and ISO 27001 compliance certifications for Quoter have been added.
How did we do it?
Using ControlMap, the same tool that we recommend for you to help your own clients on their compliance journey.
ControlMap also makes it (relatively) easy and painless to collect evidence to maintain compliance for our other ScalePad products that were already compliant, showcasing controls and evidence and sending that data to our third-party auditor.
If you’re curious about Compliance-as-a-Service as an opportunity to grow your MSP, definitely take the time to go through ScalePad's free Compliance as a Service Boot Camp and learn more.
What does this mean for you, our ScalePad Partners?
It means we’ve been through the serious annual audit and evaluation process, ensuring Quoter, Lifecycle Manager, Lifecycle Insights, Backup Radar, and ControlMap meet top-tier global standards for keeping your data secure.
With these certifications in place, you can feel confident knowing your MSP’s data is protected from threats and vulnerabilities, allowing you to stay focused on growing your business.
Where can I learn more about product security at ScalePad?
Head over to scalepad.com/security to confirm these words for yourself. Grab our updated Security Whitepaper, ISO certificate, and SOC 3 Report and verify we’re walking the talk.
Get the SOC 3 Report
Our downloadable SOC 3 report for ScalePad covers Lifecycle Manager, Lifecycle Insights, ControlMap, Quoter, and Backup Radar. The download link below will open a new tab for you to view.
Why pursue SOC compliance?
SOC 2 Type II compliance verifies that ScalePad's systems and processes safeguard Partner data against unauthorized access, use, and disclosure. Similarly, the ISO 27001 certification demonstrates ScalePad's commitment to implementing comprehensive information security management systems, encompassing policies, procedures, and controls to manage and protect sensitive information.
"Cybersecurity isn't just a box to check; it's a guiding principle,” said Zach Keller, CFO of ScalePad. “Achieving SOC 2 Type II and ISO 27001 compliance reinforces our commitment to maintaining and continuously improving our security measures. This commitment to rigorous standards demonstrates our dedication to enhancing security practices in response to evolving threats.”
“Elevating security posture while cultivating trust is at the heart of what cybersecurity compliance is all about,” said security compliance expert Dan Fox, who also works as a lead in cybersecurity education for Scalepad’s ControlMap team. “ScalePad's commitment to security and protecting our partner ecosystem is emphasized through the implementation of best practice frameworks such as SOC 2 and ISO 27001, thanks in part to ControlMap, our Security Compliance management solution used by thousands in the MSP community, including ourselves."
Furthermore, SOC 2 Type II compliance provides a higher level of assurance that data is being protected consistently over time. By undergoing a thorough Type II audit, ScalePad identifies and addresses potential security risks and vulnerabilities, mitigating the likelihood of data breaches and financial losses. Additionally, ScalePad's compliance with SOC 2 Type II standards supports its Partners' efforts to maintain regulatory compliance across various industries, including GDPR and HIPAA, by providing evidence of robust security and privacy controls.
For more detailed information about ScalePad’s commitment to product security, including our Security Whitepaper, please go to scalepad.com/security.
How did ScalePad do it?
Quickly and painlessly – ScalePad used our own product, ControlMap, to simplify our journey to cybersecurity compliance. The same multi-tenancy and templated frameworks that can help your MSP get your clients compliant helped ScalePad rapidly get multiple products compliant across two different-but-complementary frameworks.
Using ControlMap’s automated evidence collection functionality, the audit required for SOC 2 Type II compliance and the surveillance audit for ISO 27001 was straightforward. The controls, policies, and procedures were already in place, along with automated monitoring of dozens of integrated systems.
ControlMap provides ScalePad with a single platform to manage everything compliance-related internally at our organization and can enable you to do the same for your MSP’s clients. Whether you already work with clients in regulated industries or aspire to expand your service portfolio to include compliance services, ControlMap gives you the tools to get compliant yourself and to generate recurring revenue by helping your clients along their compliance journey.


