Is your MSP interested in SOC 2 compliance? Jump-start the process with our complete SOC 2 assessment guide!
In this article, you will learn:
Chances are that customers or prospects have asked you. If you don’t already have a SOC 2 report, you likely struggled to answer.
Your inability to confidently answer could be blocking a sale. That’s right — a SOC 2 examination has become the go-to standard for cybersecurity assurance for service providers.
With our work helping MSPs meet their compliance objectives, such as SOC 2, we’ve created this guide to help you with your own SOC 2 audit.
SOC 2 is an examination of your company’s security controls performed by an external certified CPA. Let’s dig into more details.
The American Institute of Certified Public Accountants (AICPA) created the SOC 2 compliance standard. It consists of Service Organization Controls (SOC 2) requirements, including an examination of your controls with an audit report.
The SOC 2 report is an outcome of an audit conducted by an external Certified Public Accountant (CPA) on the company’s compliance controls.
A SOC 2 evaluation categorizes the controls in high-level categories, known as the Trust Services Criteria (TSCs). The TSCs are security, availability, processing integrity, confidentiality, and privacy.
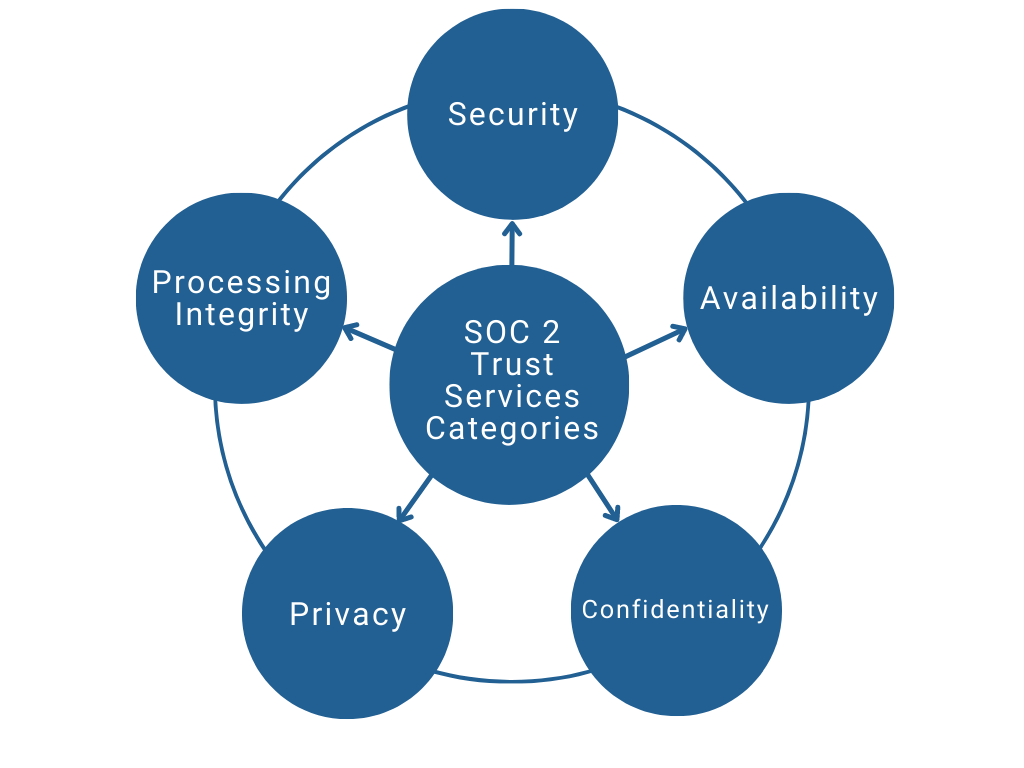
The report assures your partners that your MSP takes cybersecurity and data privacy seriously.
With a SOC 2 report, you get detailed information about your company’s security and privacy controls. Informed MSPs can address the risk management processes, vendor management processes, and other company governance processes.
| Trust Services Criteria |
|---|
| Security Evaluates the protection of Information Security Systems from unauthorized access. This includes other threats that could damage the information system’s confidentiality and availability. |
| Availability Evaluates controls related to the availability of information systems as defined by your SLA objectives. |
| Processing Integrity Evaluates controls that ensure information is processed accurately, in time, and according to your objectives. |
| Confidentiality Evaluates controls that secure and protect confidential information from unauthorized access. |
| Privacy Evaluates controls that are in place to protect the privacy of Data Subjects’ information and other data processed and stored in the system. |
So what’s a control? A control is a statement describing any management, operational, or technical method used to manage risk.
Controls monitor and measure aspects of standards to help the company accomplish their goals or objectives.
At a minimum, a SOC 2 report evaluates controls for the Security TSC. This control ensures the system is protected against unauthorized access (physically and logically).
Each TSC outlines the requirements your company must meet. They outline the points of focus that you must implement as controls to be ready for a SOC 2 examination.
Below is a high-level overview of the various TSCs and the overarching requirements included for each.
| Trust Services Criteria | Areas Covered |
|---|---|
| Security This TSC covers 33 requirements with more than 120 points of focus implemented as controls. | Security Covers Personal Conduct, Corporate governance, Awareness training, Code of Conduct, Access Control, Asset Management, Data Protection, Change Management, Hiring & Termination workflows. |
| Availability There are three additional requirements for the Availability TSC. About 15 points of focus typically implemented as controls. | Availability Covers current capacity, forecasting system usage demand, data backup, and alternate processing infrastructure. |
| Processing Integrity The criteria for Processing Integrity have five additional requirements. Making up about 14 points of focus. | Processing Integrity Covers data related to processing inputs, detection and correction of production errors, and other system processing specifications. |
| Confidentiality The criteria for Confidentiality specify requirements for an entity to identify and maintain confidential information. | Confidentiality Covers protecting, identifying, and maintaining sensitive information. |
| Privacy This TSC deals with the additional requirement for handling your customers’ and users’ private and personal data. There are eight additional requirements to be implemented and 50 points of focus. | Privacy Covers criteria related to choice, consent, and collection of private information, access, disclosure, and monitoring. |
Type 1 Report – This report evaluates the suitability of the design of the controls at a single point in time. The auditor assesses the effectiveness of control design and implementation. This report does not evaluate the operating effectiveness of the controls themselves. A Type 1 evaluation report is generally the first step for a company.
Type 2 Report – A type 2 report evaluates the design of controls and their operating effectiveness of the controls over a period of time. This period must be at least six months and no more than 12 months before the Type 2 audit. An auditor assesses the controls operating effectiveness and completeness of the evidence collected. The auditor provides an opinion and detailed description of tests of controls performed and those tests’ results.
First-timers and startups most commonly get a SOC 2 Type 1 report, followed by a SOC 2 Type 2 report. After achieving the SOC 2 Type 2 report, there usually isn’t a need for another Type 1 report.
A SOC 2 report is produced by an AICPA accredited auditor and may vary based on the company’s needs, scope, and environment. It typically contains the following information:
A SOC 2 report can help provide positive assurance to customers for many types of businesses.
However, we see that companies dealing with customer data and doing business in the cloud are the ones who most definitely need a SOC 2 Report. Most SaaS companies and software service providers fall in this category.
For other enterprises and businesses, SOC 2 may or may not be the right choice. They may choose to pursue other cybersecurity certifications such as ISO 27001, NIST CSF, or others.
It takes anywhere from 30 days to one year to be ready for a SOC 2 audit. The time varies depending on the organization’s size, complexity, the scope of the products and services, and preparedness for a SOC 2 audit.
A Type 1 SOC 2 audit typically lasts two to three weeks, while a Type 2 SOC 2 audit can last up to six weeks to complete.
Here’s what we see works best to get off the ground for SOC 2:
Now you know where and how to start, the next step is to define a plan with timelines to keep you on track for your SOC 2. You will typically create this plan in collaboration with your service provider and auditor. Here’s what a typical plan looks like:
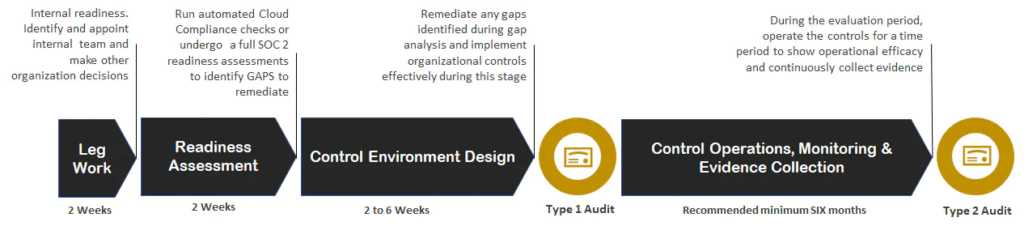
These durations are highly company-dependent and sometimes could take more than a year. ControlMap can cut down readiness and control design time by 90%. It has its built-in controls and evidence collection connectors to help you work faster.
Legwork is about getting started. It’s all about company internal readiness, teams, objectives, and other scope exercises that we discussed.
In this phase, you and your readiness consultant assess where you stand and what gaps must be addressed.
You’ll also decide which readiness assessment approach works for you based on your company’s maturity, products, and services.
A SOC 2 readiness assessment guides you through a Yes / No questionnaire to identify gaps. This helps you develop a list of to-do’s before you are audit-ready.
You may also want to perform an automated cloud compliance check. Start here if your products and services are in cloud environments such as AWS, Azure, or Google Cloud. An automated scanner checks your Cloud configuration against security standards. It will present a list of areas that need remediation.
There are four key activities that are typically performed in this stage:
The information assets inventory is a crucial information security assurance principle.
Every single information asset in the organization’s infrastructure must be accounted for and listed. This includes information sources and systems, physical computing assets, licensed software assets, and open-source software assets used within the in-scope control environment.
This phase aims to identify the critical risks your business faces and create mitigating controls for those risks.
Risks vary based on the business environment. But there are common risks for cloud businesses, software products, and services that you should mitigate. A formal periodic Risk Assessment guides your team in identifying critical risks. They can then assign scores, and review controls to mitigate those risks.
During this step, you design and define controls based on the assessment gaps and identified risks. You identify owners for each control and define the evidence that has to be collected and its frequency.
Here are the most critical control areas for defining controls for a successful SOC 2 audit. You can sign up for free to look at all controls required for SOC 2.
| Control Areas, Objectives, and Samples |
|---|
| Human Resource Management Establish policies and procedures relating to the area of Human Resources. These controls typically apply to procedures such as employee background verification, hiring & termination, employee handbooks, code of conduct, etc. • Employee Handbook. • Job descriptions, including security. • Background Screening Policy and Procedures. • Hiring & Termination processes and checklists. • Employment agreements. |
| Security Awareness & Training Establish policies and procedures relating to the company workforce’s security awareness and training to prevent data loss and theft. • Annual security awareness training. • Role-based security awareness training. |
| Risk Management Procedures Conduct an annual risk assessment to identify critical risks to the company and perform a risk mitigation exercise. • Annual risk assessment, report, and treatment plan. |
| Identity & Access Control Establish controls to restrict user access to sensitive information and document policies and procedures for granting and revoking access to information systems. • Centrally manage all users & identities in the company. • A strong password policy is defined for all sensitive systems. • Enable multi-factor authentication to sensitive and administrator access and other sensitive areas. |
| Application & Information Security The objective of this control area is to define and maintain application development and operation security standards. • All code development follows security standards such as OWASP. • Establish baseline security configuration for all applications and systems. • Separate software development, QA / testing, staging, and production environments. |
| Cryptographic Protection This control area aims to define cryptographic protection for data at rest and data in transmission. • All databases are encrypted. • Protect all data transmission using secure protocols, i.e., HTTPS, TLS. • All sensitive removable storage is encrypted. |
| Threat & Vulnerability Detection Establish, document, approve, communicate, apply, evaluate and maintain policies and procedures to identify, report, and prioritize the remediation of vulnerabilities to protect systems against vulnerability exploitation. Review and update the policies and practices at least annually. • Malware Protection Policy and Procedures. • Perform quarterly penetration testing. – Perform application vulnerability testing & detection each quarter. |
| Logging & Monitoring This control area establishes policies, procedures, and controls for enabling logging for all user access, administrative access and monitors them to detect anomalies in access patterns and security incidents. • Retain audit logs for at least 60 days or longer to support investigations. • Monitor security logs to detect activity outside of known patterns. • Log and monitor cryptographic key user lifecycle events. |
| Change Management This control area establishes policies and procedures for making changes in the environment. • Centrally track all application changes. • Production changes require explicit approval. • The security team reviews Security-related changes. |
Within each Trust Services Criteria, there are four main sections during the audit period.
Policies: Company has defined and documented its policies relevant to the particular principle.
Communications: Company communicates its policies to responsible parties and users of the system.
Procedures: Company changes operation procedures to match its defined policies.
Management and Monitoring: Company monitors the system and acts to maintain compliance with its defined policies.
A SOC 2 evaluation requires the following policies established and documented:
During this focused period, your company operates the designed controls. You will continuously monitor them and collect evidence about the controls’ proper functioning.
The activities during this period are continuous. Evidence collected is specific to the environment, controls, products, and services. Illustrative activities and the evidence that must be collected are following:
| New hire • List of new hires. • Proof that background checks were conducted. • Proof that access authorizations were approved. • Proof of employment contract and handbook signatures. • Proof that terminated employees’ assets were returned. |
| Change management act • List of change tickets for the examination period. • Proof of change management approval. |
| User access provisioning • List of approvals for administrative access. • List of access requests. • Proof of role-based access. • List of privileged and least functional access. |
| Application Vulnerability Scans • Quarterly vulnerability scan reports. • Proof of vulnerability remediation. |
| Penetration Testing Reports • Proof of penetration testing performed by a third-party. • Proof of penetration testing findings and remediation. |
You can automate and streamline up to 90% of evidence collection. A platform like ControlMap continuously monitors your cloud environment, HR systems, and vulnerability scanning tools. It helps you stay up to date with compliance at all times.
The cost for your SOC 2 will vary and will depend on the scope you select and the complexity of your company’s products and services. Typically the SOC 2 cost is comprised of the following components:
All combined, a SOC 2 report can be a costly affair. A typical audit can cost upwards of $40,000 for a Type 1 and Type 2 report.
Additional services such as internal audits and service providers for penetration testing range from $15,000 to $50,000. The price can be higher depending on other factors. Those include the control environment scope, information security maturity, and staff participation.
Yes, it is absolutely worth it! A SOC 2 Report impacts your business reputation and its ability to compete in the market today. It sets up acceptable security practices and even improves operational effectiveness.
ControlMap is ready to help you get started on your SOC 2 journey. For more information on how ControlMap helps you follow the path to compliance with SOC 2 or other frameworks, book a demo today.