Cognition360 has released enhancements to 4 reports that provide your MSP with improved analysis of your operations and financial measures, including two core reports. Just like the set of reports we updated in March, however, you have to ask for them to get them.
Let’s take a quick look at each of the new-and-improved reports and see exactly what’s new and improved.
Here’s the list:
You might not be using all of these reports now, but they’re all well worth a second look.
The Cognition360 Support team’s got what you need. If you know exactly what you want, you can fill in this form and request to have the report you want updated to the latest version. Next step, you’re in and using them.
The official word from our Product team is that “these improvements will improve customer retention, enhance your quality of life, and empower you to make more informed and strategic business decisions.”
Are we over-promising? I’d sure like to enhance the quality of my life. Read on to learn more about each; you be the judge.
Yes, we just updated this a few months ago, but it’s even better now.
The Opportunity Dashboard now shows the latest conversion stage with the latest conversion value. This will help avoid any confusion, as it will only show the latest stage and value instead of multiple conversion stages with different values. Feedback was that the granularity of multiple conversion stages was more trouble than it was worth.
The report now uses the actual last invoiced amount to improve accuracy.
The enhancement to the Agreement Renewals Report improves it to use the actual last invoiced amount as renewal amount instead of amount of the agreement. This better represents true renewal values, as the actual amount can be different from agreement amount. This allows you to see the effects of discounts or deals – how much are your clients actually being charged?
The Service Profitability Report has been updated with ticket summary, board, and billability status.
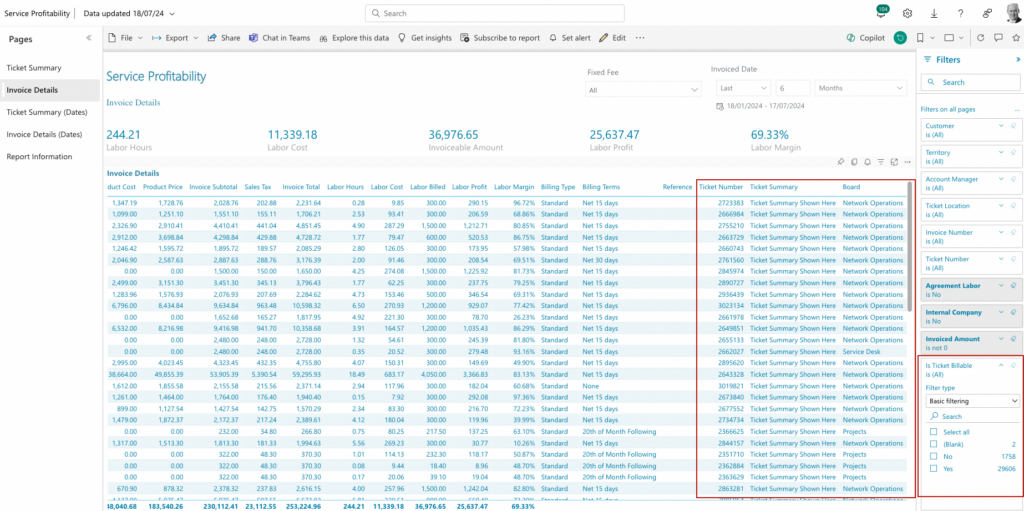
The report itself has been updated to display Invoice Details with a ticket summary. Scroll to the right, and you’ll see an at-a-glance overview of each ticket, and the ability to sort by which board tickets were assigned to – another way to look at cost/profit/margin by ticket on each service board.
A “Is Ticket Billable” filter has also been added, allowing you to filter out ticketed-but-non-billable work that you may choose not to include in your profitability reporting. This allows you to maintain best practices of tracking all work with tickets and time entries without distorting your margin measures; for example, when team members may be assigned to non-revenue internal projects.
Three enhancements have been made to Ticket Daily Stats:
Want to see right from the Ticket Daily Stats report who’s been sending in tickets and get a hold of them for follow up? Contact is now listed right there.
The Tickets Resolved page now displays the average age of resolved tickets and compares the average age of those resolved tickets by day, week, and month. The Ticket Age calculates the time elapsed between the ticket creation date and the resolution date.
A new page, Ticket Owner | Ticket Resolved, allows a ticket owner to see all their resolved tickets, regardless of who actually resolved them. Perfect for when you’re coming back from summer vacation and you want to know who to thank for closing out some tough ones.
Speaking of summer, we’ll have more updated reports at the end of it. Please use the form to request any of these that interest you, and keep your eyes peeled for more enhancements to Cognition360.
Already a partner? Check this post out and discuss on our Community site.
Not a Cognition360 partner yet? Join us for a personalized demo, or check out this quick overview here. We’d love to help you unlock your ConnectWise PSA data to make better decisions and grow a more profitable MSP business.
Preparing for and completing audits of frameworks and controls requires meticulous planning and execution. ControlMap has upgraded the audit experience in-app to further streamline the process and eliminate more tedious tasks from the to-do list with internal audits, jumpstart expansions, evidence exports, and updated vendor reports.
Internal Audits
MSPs and their clients can now perform an internal audit based on either frameworks or controls. Previously, audits were limited to third-parties, but we’ve provided the ability to perform this internally for a framework or a control set. This offers MSPs and their clients the following benefits:
Not every MSP or client requires a third-party audit based on the organization, vertical, and compliance goals. While compliance with a certain standard may be the goal for many businesses, all organizations strive to improve their security operations. An internal audit helps support organizations earlier in their compliance journey to strengthen their security posture by identifying potential gaps and addressing them.
The internal audit feature also allows MSPs and their clients to perform robust self-assessments to ensure they meet the required standards and guidelines of frameworks that rely on self-assessment. It documents evidence of assessment (or audit) history, risks, evidence, and more that can be referenced as required in their industry.
Cross-mapping and Jumpstart Expansion
Many organizations need to satisfy the compliance requirements across multiple frameworks. ControlMap helps streamline the process by cross-mapping frameworks to identify common items required for assessment. Jumpstarts apply matching evidence to other frameworks to reduce the amount of labor. Support for the following jumpstarts is now available:
Evidence Export
For CMMC compliance audits, auditors require submission of all evidence of compliance. With a single click of a button, ControlMap users can export all evidence required by auditors including:
MSPs no longer have to cobble together and create an audit-friendly file & folder structure anymore – this is all automated to streamline the audit preparation process and remove friction from the audit itself. While developed particularly with CMMC in mind, the evidence export is useful across all compliance frameworks as it creates an evidence record that can be archived and accessed if required.
Vendor Reports
A key piece of compliance is tracking risks associated with vendors that have access to any sensitive information or data. Ad hoc export of vendor data had been possible, but ControlMap has now added the ability to schedule and save vendor reports. These reports are audit-ready making preparation for a third-party audit effortless – no more struggling to format excel sheets or word documents.
Automation is the best friend of an MSP – it eliminates tedious manual work. With the latest enhancements to the audit experience, ControlMap can put hours back in your team’s day. Log in to ControlMap to start enjoying an enhanced audit experience.
ControlMap now supports the NIST AI Risk Management Framework, enabling MSPs to support cybersecurity programs related to AI.
The NIST AI Risk Management Framework (AI RMF) is a security standard developed by the National Institute of Standards and Technology (NIST) to help manage the risk of generative Artificial Intelligence (AI). It was developed through a transparent, collaborative process and released in 2023.
The framework is designed to help organizations involved in the design, development, use, or regulation of AI technologies, to better manage risks associated with AI as well as incorporate trustworthiness into AI products.
NIST AI RMF is intended for voluntary use. It aims to align with and build upon AI risk management efforts already in place.
The benefits of NIST AI RMF
NIST AI RMF aims to help organizations manage risks associated with AI through a proactive and ethical approach. Organizations that implement this framework get the following benefits:
The framework offers detailed guidance on establishing robust governance practices for AI deployments. This helps organizations create clear policies and procedures that govern AI use, ensuring compliance with regulatory requirements and alignment with business objectives.
By adopting the NIST AI RMF, organizations can better identify, assess, manage, and monitor risks associated with AI technologies. This structured approach allows for more proactive risk management, reducing the potential for adverse impacts on the organization or any of its stakeholders.
NIST AI RMF helps organizations ensure their AI systems are reliable and trustworthy by providing a framework that emphasizes accountability, transparency, and the ethical use of AI. This can lead to increased user confidence and a stronger reputation for organizations deploying compliant AI solutions.
It’s time for your clients to ensure risks related to their work with AI is minimized. ControlMap Partners can now import the NIST AI RMF framework to their clients’ tenants, cross-map against current frameworks, and get started addressing any gaps. Login to ControlMap to get started on NIST AI RMF now.
For more information or to learn about jumpstarting your own vCISO services with NIST AI RMF, request a demo.
ControlMap now supports the Digital Operational Resilience Act, enabling MSPs to implement cybersecurity programs for financial institutions operating within the European Union.
The Digital Operational Resilience Act (DORA) is an EU regulation aimed at strengthening the cybersecurity and operational resilience of the financial sector within the European Union. It is critical for financial institutions as it mandates comprehensive management of IT risks, ensuring consistent and robust security practices across the sector to prevent and mitigate cyber incidents.
Before DORA, financial institutions mainly managed risks with the allocation of capital, but they didn’t focus on all aspects of operational strength. After DORA, these institutions need to follow specific rules for protecting against, detection, containment, and recovery capabilities for IT-related incidents. DORA sets specific guidelines for IT risk management, incident reporting, information sharing, digital operational resilience testing, and third-party IT risk management.
DORA is a requirement for financial institutions to be in compliance with EU regulations. Compliance is required to protect financial institutions from regulatory penalties due to non-compliance. Organizations deemed non-compliant may face significant penalties that are imposed on a daily basis to encourage compliance. They may also be subject to a periodic penalty payment of 1% of their average daily global turnover in the preceding year. Outside of financial penalties, non-compliant organizations may be issued termination notices, cease-and-desist orders, and/or public notices.
However, the implementation of DORA also brings benefits that strengthen operations including:
Financial Institutions in the EU are required to be compliant with DORA. ControlMap Partners can now import the DORA framework to their clients’ tenants, cross-map against current frameworks, and get started addressing any gaps to avoid regulatory penalties. Sign to ControlMap to get started on DORA now.
For more information or to learn about jumpstarting your own vCISO services with DORA, request a demo.
Maintaining security to defend against cybersecurity threats is a never-ending process. MSPs have to continually monitor networks, assets, and more for vulnerabilities and close any gaps they find.
Now, there’s an easier way to monitor clients for vulnerabilities. ScalePad has integrated ControlMap with ThreatMate to automate vulnerability & compliance checks required to achieve and maintain compliance.
ThreatMate is an advanced attack surface management tool designed to monitor and secure networks from various cybersecurity threats. This comprehensive platform scans both external and internal network environments, including behind the firewall, and extends its monitoring capabilities to cloud services like Microsoft O365 and Google Workspace. By leveraging artificial intelligence and machine learning, ThreatMate identifies security exposures and creates targeted mission plans for vulnerability remediation, ensuring a secure cyber environment across all connected devices and endpoints.
MSPs that use ThreatMate achieve the following benefits:
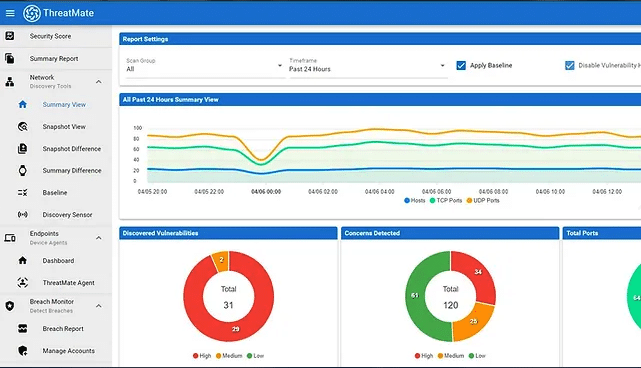
Integrating ControlMap and ThreatMate allows for automatic collection of scan results by company and mapping to frameworks. It can be configured to run a scan and update the results weekly for continuous checks and updates.
Collection of evidence – Once you’ve connected ThreatMate to ControlMap, the connection automatically starts collecting the following data from ThreatMate scans on a weekly cadence:
Mapping to frameworks – The collected evidence is then mapped to over 50 security and compliance frameworks, such as SOC 2, ISO 27001, HIPAA, FTC Safeguards, CIS Controls, CMMC, and other frameworks and security standards. Mapping the evidence automatically provides a detailed view of any gaps that need to be addressed.
Ongoing automatic updates – The ControlMap-ThreatMate integration is not simply a one-time check. ControlMap can be configured to regularly sync with ThreatMate to provide up-to-date evidence & vulnerabilities. This will update the evidence based on the current settings, ensuring that your team is aware of any configuration changes, new risks or gaps so you can take remedial action to maintain compliance.
Connecting ControlMap and ThreatMate reduces hours of manual data imports and regular reviews. It automatically retrieves, updates, and stores current evidence required for compliance frameworks so your team can focus on maintaining and improving security.
Combine the capabilities of ThreatMate with ControlMap now. Login to your ControlMap instance to get started. For more information or a discussion on how to elevate your compliance operations, request a demo.
ControlMap now supports the NYDFS Cybersecurity Regulation, enabling MSPs to tailor cybersecurity programs for clients operating under the New York State Department of Financial Services jurisdiction.
The New York State Department of Financial Services (NYDFS) Cybersecurity Regulation, known as 23 NYCRR 500, is a cybersecurity framework for financial institutions operating under NYDFS jurisdiction.
Established in March 2017, NYDFS mandates stringent security standards, requiring financial institutions to maintain secure data systems and reduce vulnerabilities. It covers organizations such as banks, insurance companies, credit unions, and their third-party service providers. To be compliant, institutions operating under NYDFS jurisdiction must ensure their cybersecurity practices align with the regulation’s standards.
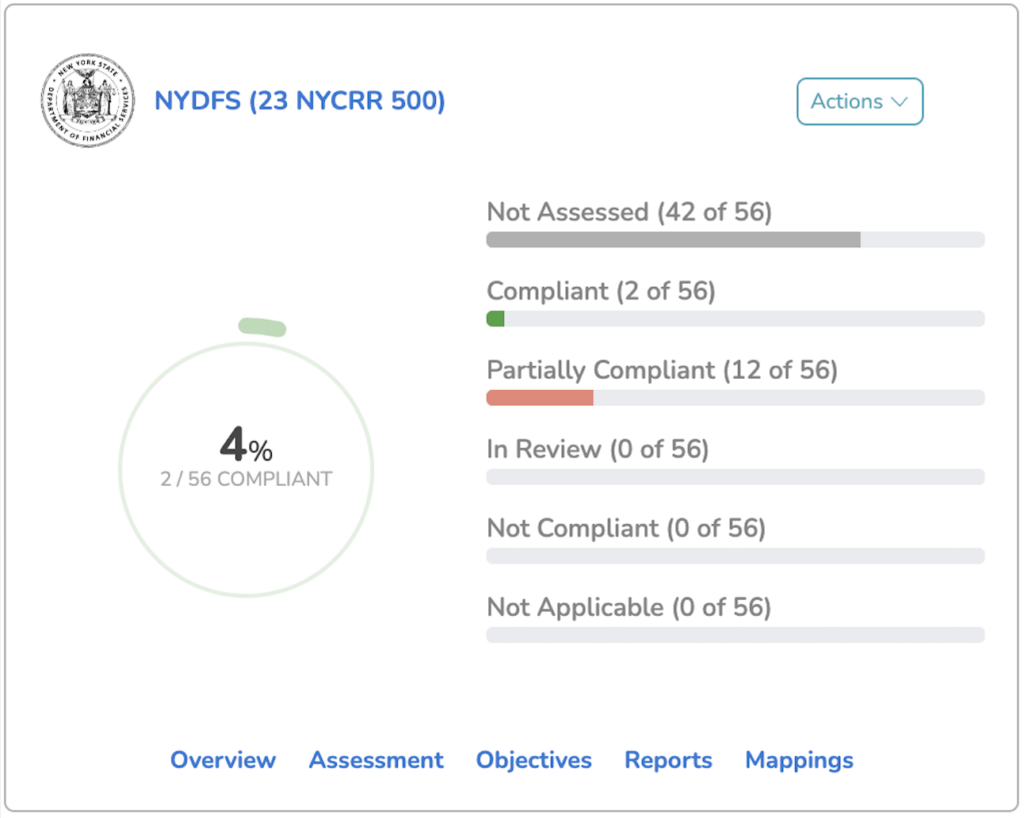
While the NYDFS Cybersecurity Regulation is a requirement for financial institutions, it does provide further tangible benefits to these organizations. Implementing the framework leads to:
Implementing the NYDFS Cybersecurity Regulation helps financial institutions achieve stronger security and compliance, empowering them to manage risks while building trust with clients.
It’s time for your clients under NYDFS jurisdiction to have peace of mind that they are compliant with all regulations. Login to ControlMap to get started on NYDFS now. For more information or to learn about jumpstarting your own vCISO services with NYDFS, join a demo.
Meet the new Lifecycle Manager — a unified place to assess, plan, implement, and measure meaningful changes for your clients.
With Lifecycle Manager for client engagement, MSPs of all sizes can improve the quality and productivity of their interactions with clients, including QBR/vCIO preparation and managing the entire client lifecycle at scale. We’ve made it possible to cut QBR prep to minutes, not hours, so all MSPs, regardless of operational maturity, can reinforce their position as a strategic partner to their clients with efficiency and professionalism.
“It’s super-exciting for us to bring a platform to market and iterate that platform to solve the rapidly growing challenges of being an MSP in this highly competitive industry,” said Chris Day, ScalePad Founder and Chief Product Officer. “Rallying around their biggest asset — their people, both within their organization and their clients — to drive positive change and true impact is essential to scaling an MSP and retaining happy clients,” he continued.
The new Lifecycle Manager includes an updated interface, enhancements to existing features, and game-changing additions to bring client-focused tasks to the forefront, helping you improve client experience and reinforce your position as a strategic partner. Here’s a closer look at what you get in the new Lifecycle Manager:
We’ve overhauled the dashboard to prioritize client activity. Elements such as the Client tab now sit along the top of the dashboard, saving you time with a more efficient client-focused workflow. These small yet mighty changes help streamline how you keep a pulse on the technology health of all of your clients.

Become an expert on every one of your clients. Our enhancements to the client strategy dashboard give you a central hub for engagement and strategy on a client-based level. The information you need to inform your next QBR or vCIO meeting is at your fingertips.

The new client strategy dashboard lets you log meeting notes, store and update key contact information, and publish Action Items that can be automatically submitted as tickets in your ConnectWise Manage PSA. With these updates, we’ve eliminated the need for toggling between your PSA, notebooks, and other tools for tracking and executing meeting follow-up tasks.

We think getting buy-in from your clients on strategic initiatives should be easy. With a new layout that integrates Initiatives into Roadmaps, you can create crystal-clear plans that are easy for non-technical clients to understand and view at a glance in the day-to-day maintenance of client experience.

You can plan up to five years on Roadmaps, which our Partners love for helping their clients prepare their budgets and anticipate what comes next. By bringing Initiatives into the roadmap view, we’re helping you create those plans ever faster by simplifying the workflow. You can drop new Initiatives into existing Roadmaps, letting you respond quickly to client needs and maintain accurate work plans.
New sharing tools let you publish and send customizable Roadmap PDFs, giving you control over the level of detail displayed and a real-time presentation mode for screen sharing.
The new Lifecycle Manager enables MSPs of all sizes to communicate efficiently using a simplified data-driven approach with their clients, encouraging trust and collaboration on strategic initiatives.
“You know you’ve achieved successful client engagement when your clients start saying yes to the obvious things that are better for them (and by proxy, you),” said Day. “It’s when your team and your clients are on the same page about what is happening now, what needs to happen, and how you will get there together.”
We’ve made it possible to prepare for your next strategic conversation in a few clicks. Try out the new Lifecycle Manager today.
At ScalePad, we’re constantly striving to equip our MSP partner community with the tools they need to excel in managing cybersecurity compliance. Today, we’re excited to announce a significant upgrade to our MSP Dashboard, designed to streamline the way MSPs interact with data and assess their client’s compliance status.
Why a new MSP Dashboard?
Our decision to revamp the MSP Dashboard stems from a deep understanding of the challenges faced by MSPs in maintaining compliance across multiple clients. Recognizing the opportunity to enhance the ControlMap MSP dashboard to address these roadblocks, we set out to create a solution that would enable MSPs to monitor client risks more efficiently.
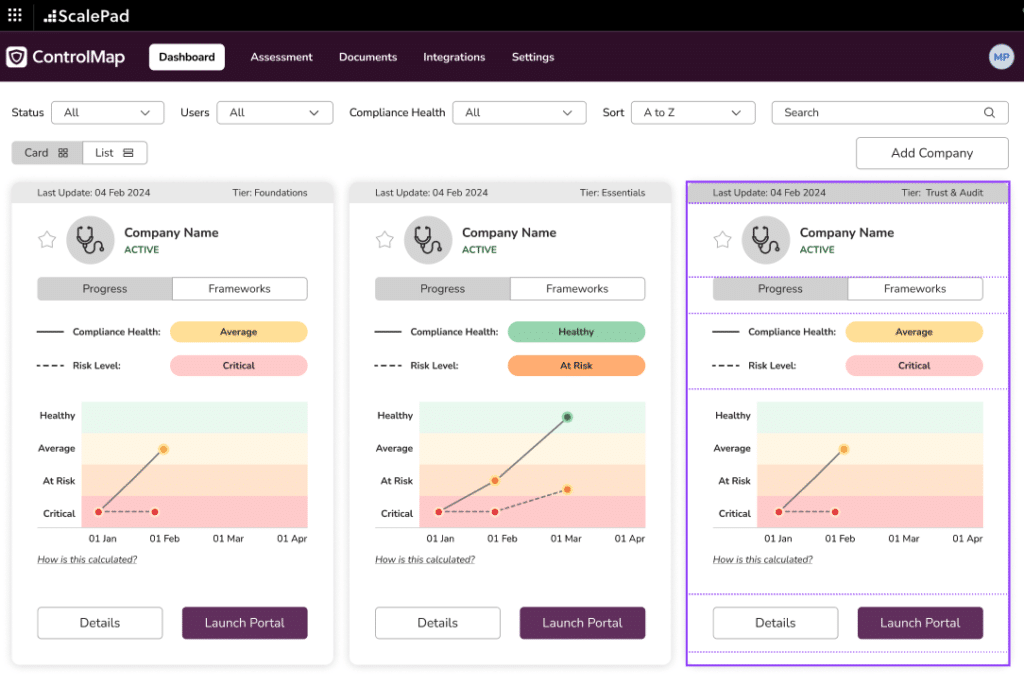
What’s New?
The enhanced MSP Dashboard is more than just a facelift; it represents a fundamental shift in how MSPs interact with compliance data. Here are the highlights:
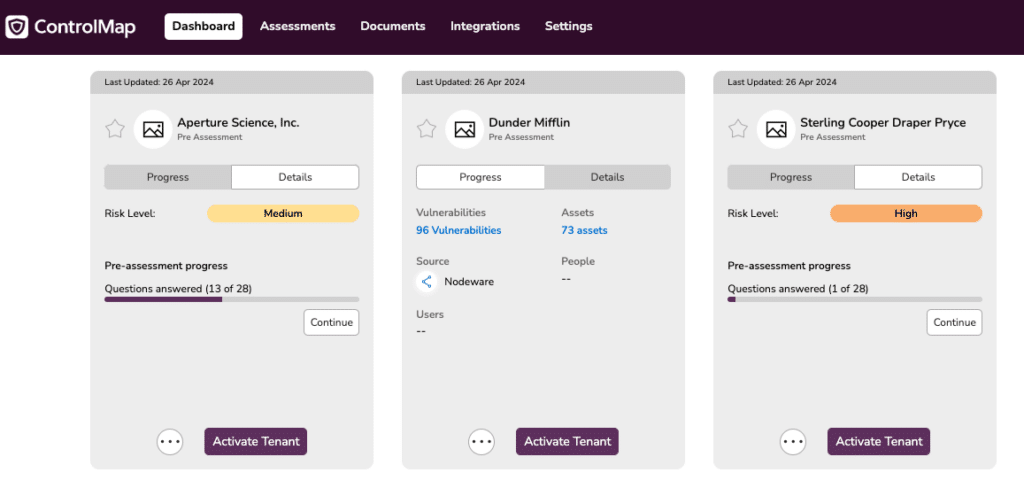
What Does This Mean for MSPs?
The enhanced MSP Dashboard isn’t just about improved functionality; it’s about helping our partners to thrive in offering compliance as a service. By providing a centralized hub for monitoring compliance and managing risks and completing pre-assessments for prospecting, we’re arming partners with the tools needed to deliver exceptional service to clients and stay ahead of emerging threats.
Get Started Today!
Ready to experience the future of cybersecurity compliance management? The enhanced MSP Dashboard is now live and available for all MSP partners. Log in today to explore the new features and take your oversight capabilities to the next level.
Stay tuned for more updates and enhancements as we continue to innovate and support our partners in their mission to safeguard digital assets and protect against cyber threats.
ScalePad is proud to announce SOC 2 Type II and ISO 27001 compliance certifications for its products Lifecycle Manager, Lifecycle Insights, Backup Radar, and ControlMap. This milestone reinforces ScalePad’s unwavering dedication to upholding the highest data security, privacy, and integrity standards for its global customer base.
Our downloadable SOC 3 report for ScalePad covers Lifecycle Manager, Lifecycle Insights, ControlMap, and Backup Radar.
SOC 2 Type II compliance verifies that ScalePad’s systems and processes safeguard Partner data against unauthorized access, use, and disclosure. Similarly, the ISO 27001 certification demonstrates ScalePad’s commitment to implementing comprehensive information security management systems, encompassing policies, procedures, and controls to manage and protect sensitive information.
“Cybersecurity isn’t just a box to check; it’s a guiding principle,” said Dan Wensley, CEO of ScalePad. “Achieving SOC 2 Type II and ISO 27001 compliance reinforces our commitment to maintaining and continuously improving our security measures. This commitment to rigorous standards demonstrates our dedication to enhancing security practices in response to evolving threats.”
“Elevating security posture while cultivating trust is at the heart of what cybersecurity compliance is all about,” said security compliance expert Dan Fox, who also works as a lead in cybersecurity education for Scalepad’s ControlMap team. “ScalePad’s commitment to security and protecting our partner ecosystem is emphasized through the implementation of best practice frameworks such as SOC 2 and ISO 27001, thanks in part to ControlMap, our Security Compliance management solution used by thousands in the MSP community, including ourselves.”
Furthermore, SOC 2 Type II compliance provides a higher level of assurance that data is being protected consistently over time. By undergoing a thorough Type II audit, ScalePad identifies and addresses potential security risks and vulnerabilities, mitigating the likelihood of data breaches and financial losses. Additionally, ScalePad’s compliance with SOC 2 Type II standards supports its Partners’ efforts to maintain regulatory compliance across various industries, including GDPR and HIPAA, by providing evidence of robust security and privacy controls.
For more detailed information about ScalePad’s commitment to product security, including our Security Whitepaper, please go to scalepad.com/security.
Quickly and painlessly – ScalePad used our own product, ControlMap, to simplify our journey to cybersecurity compliance. The same multi-tenancy and templated frameworks that can help your MSP get your clients compliant helped ScalePad rapidly get multiple products compliant across two different-but-complementary frameworks.
Using ControlMap’s automated evidence collection functionality, the audit required for SOC 2 Type II compliance and the surveillance audit for ISO 27001 was straightforward. The controls, policies, and procedures were already in place, along with automated monitoring of dozens of integrated systems.
ControlMap provides ScalePad with a single platform to manage everything compliance-related internally at our organization and can enable you to do the same for your MSP’s clients. Whether you already work with clients in regulated industries or aspire to expand your service portfolio to include compliance services, ControlMap gives you the tools to get compliant yourself and to generate recurring revenue by helping your clients along their compliance journey.